GSuite
This topic provides information about configuring a Google Workspace connector for OpenIAM. Google Workspace refers to Google Apps that consist of tools for communication, collaboration, storage, and access management.
Pre-configuration steps
You need to create a service account and its credentials. During this procedure, you need to gather information that will be used later for the Google Workspace domain-wide delegation of authority and in your code for authorization with your service account. Perform the following steps:
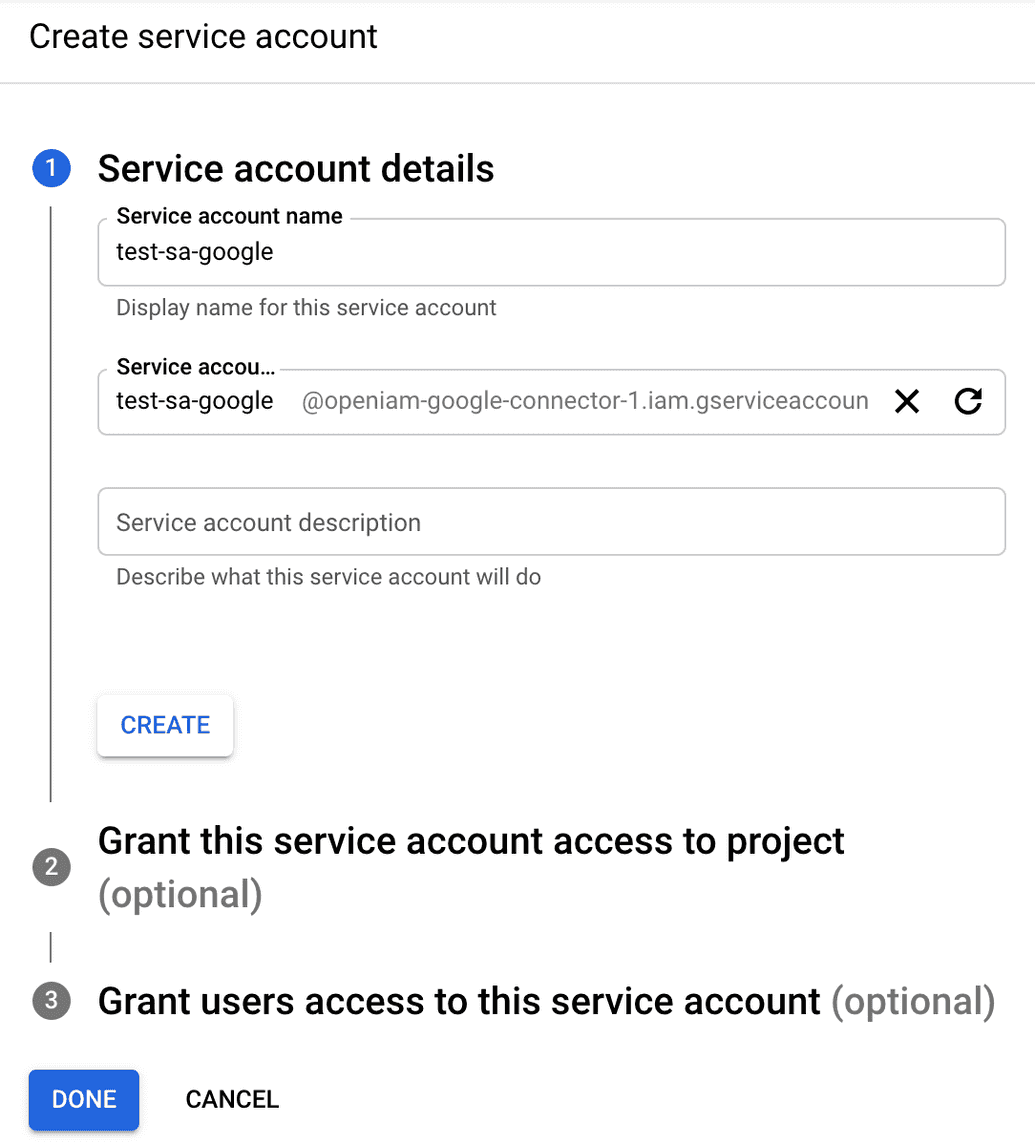
1. In Google Workspace, create the service account and its credentials by clicking on the following link:
https://console.cloud.google.com/iam-admin/serviceaccounts
Select your project
For Project role, specify Owner.
Find your service account and select Manage Keys.
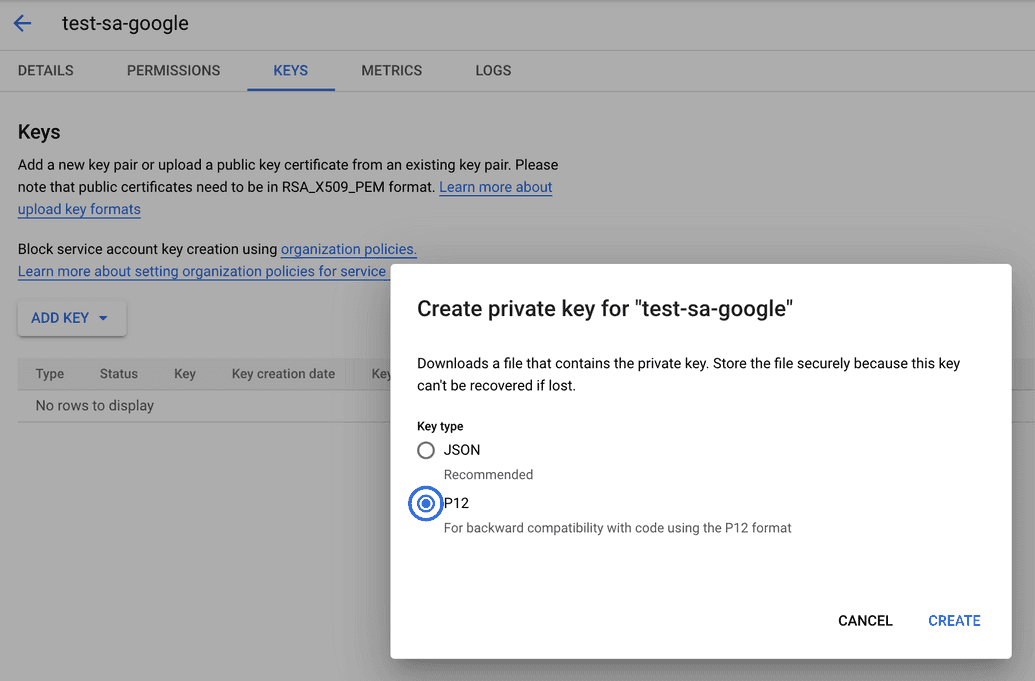
Click 'Add Key' and select P12
Your new P12 key is generated and downloaded to your machine; it serves as the only copy of this key. You are responsible for storing it securely.
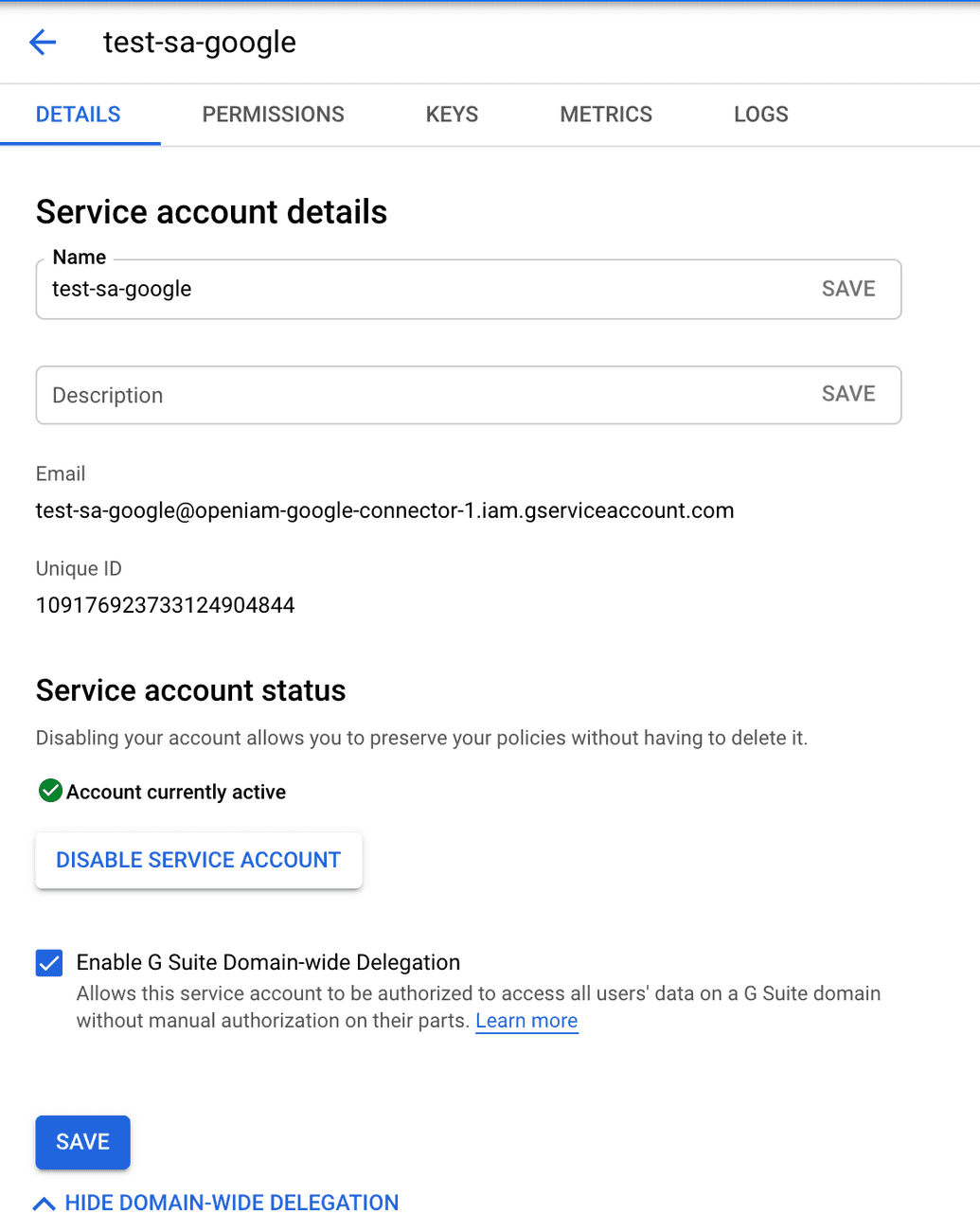
After downloading the file and closing the dialog, you will be able to get the service account's email address and Unique ID.
Delegate domain-wide authority to your service account by selecting "Enable Google Workspace Domain-wide Delegation" under "Detail" tab.
2. Add scopes for your service account.
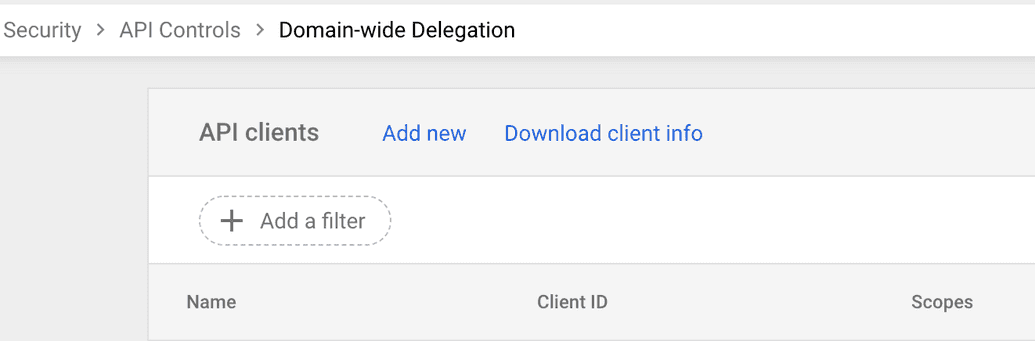
Log into the Admin Console:
Go to Security → API Controls → Manage Domain-wide Delegation → Add New
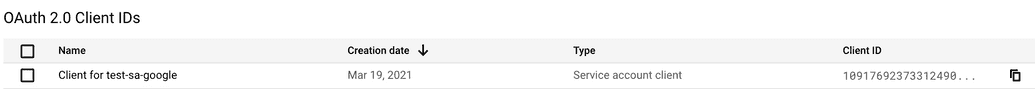
NOTE: Client ID is the unique ID of your service account (https://console.cloud.google.com/apis/credentials → OAuth 2.0 Client IDs section)
Add the following scopes (copy and paste, they are comma separated):
https://www.googleapis.com/auth/admin.directory.user,https://www.googleapis.com/auth/admin.directory.group,https://www.googleapis.com/auth/drive.file,https://www.googleapis.com/auth/driveEnable Admin SDK API.
https://console.cloud.google.com/apis/dashboard → Enable APIs and Services → Search For Admin SDK -> Enable
NOTE: if you would like to use Google Drive, you need enable Google Drive API in the same way
Configuring OpenIAM
Perform the following steps to configure the managed system to enable connectivity to the target system:
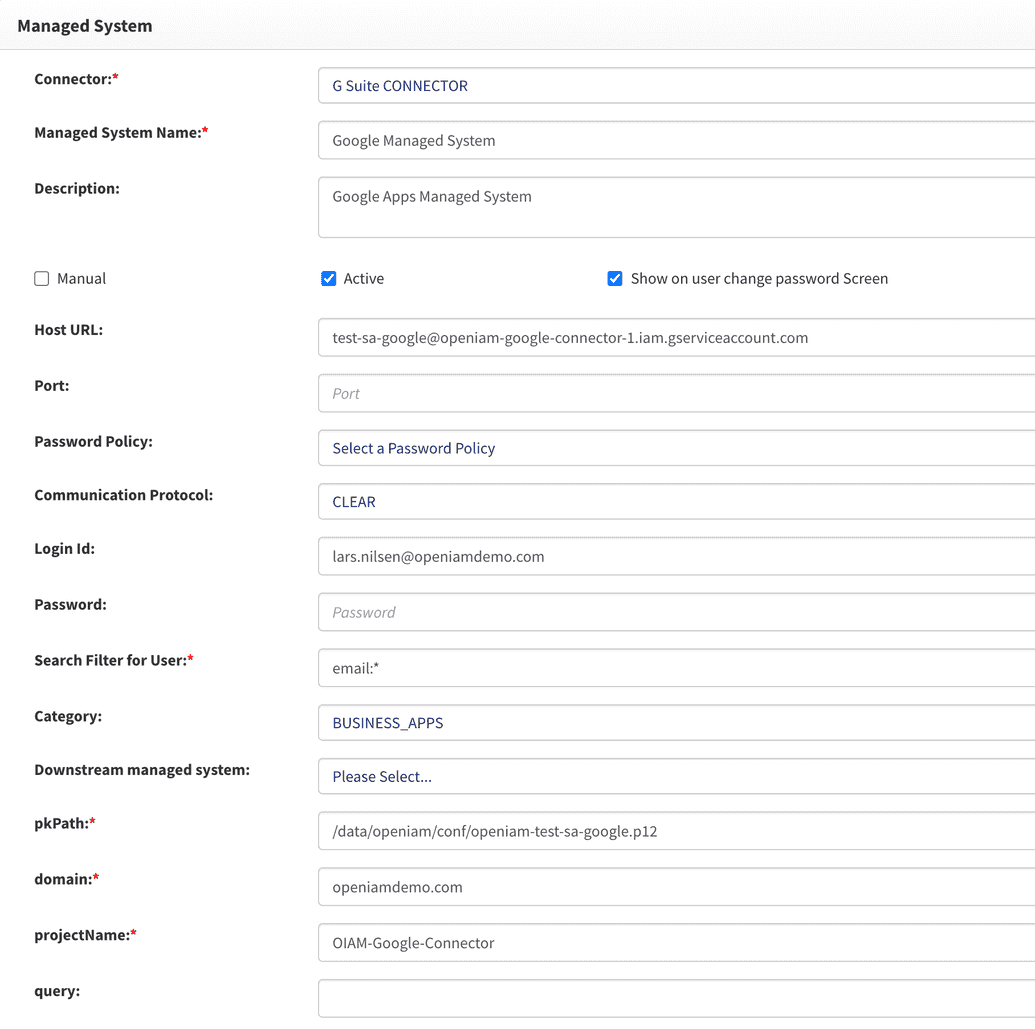
1. In Webconsole, click on the Provisioning tab and select Managed System.
Out of box OpenIAM provides predefine managed system for google (Google Managed System). You can use this one or create new.
2. Fill out information
The table below describes the fields in the Managed System page that required for Google Managed System.
| Field | Configuration |
|---|---|
| Host URL | Your service account name |
| Login ID | The login ID for the Google Workspace (Google Apps) account. The specified login ID must have admin privileges. |
| Search Filter for User | Google Search Filter. See for reference https://developers.google.com/admin-sdk/directory/v1/guides/search-users |
| pkPath | Path to the private key given to you for your Google services account that allows for authentication with the key (see Pre-configuration steps). |
| domain | The name of the Google domain. |
| projectName | The name of the Google project. |
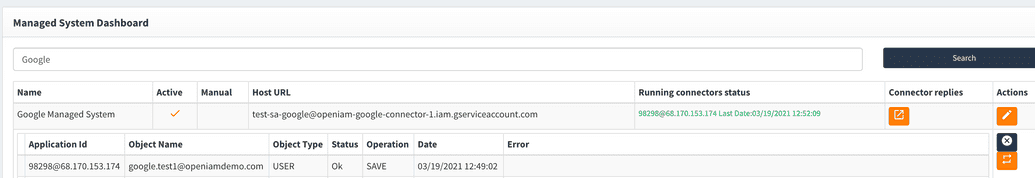
In case all configs are correct you will see green message on Managed System Dashboard page.
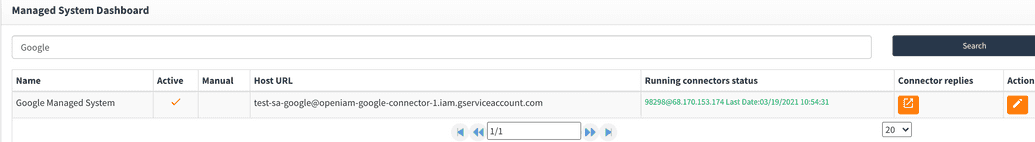
Provision to Google (Sample Example)
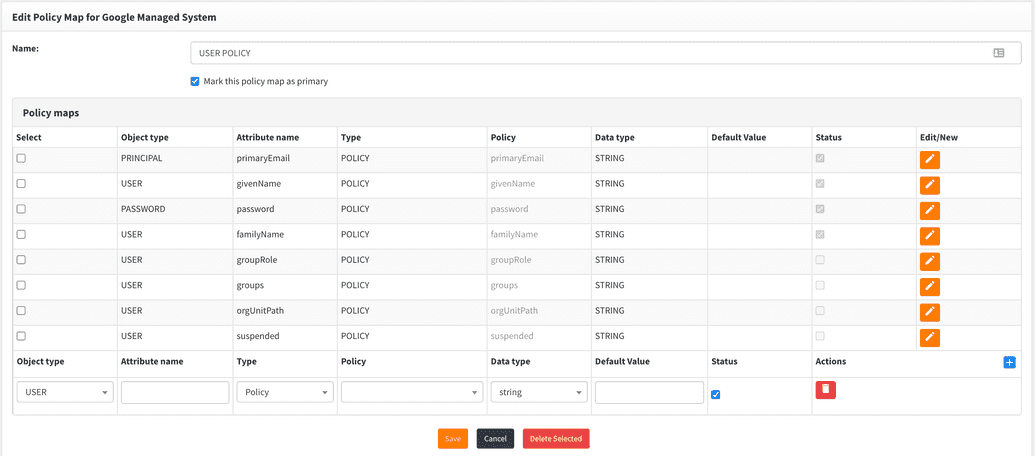
The policy map is a mapping between the attributes that are needed by the Google connector and a set of attribute policies that provide the value for each of these attributes.
The Google Apps connector uses a fixed set of attributes. The attribute map is predefined in the default Google Managed System. Typically, the correct policy map for your Google Managed System exists in the system, and you do not need to update it.
To view the policy map for the default configuration, click on the Policy Map tab in the left menu navigation pane. This displays the Policy maps for managed system page.
User Policy Map Example
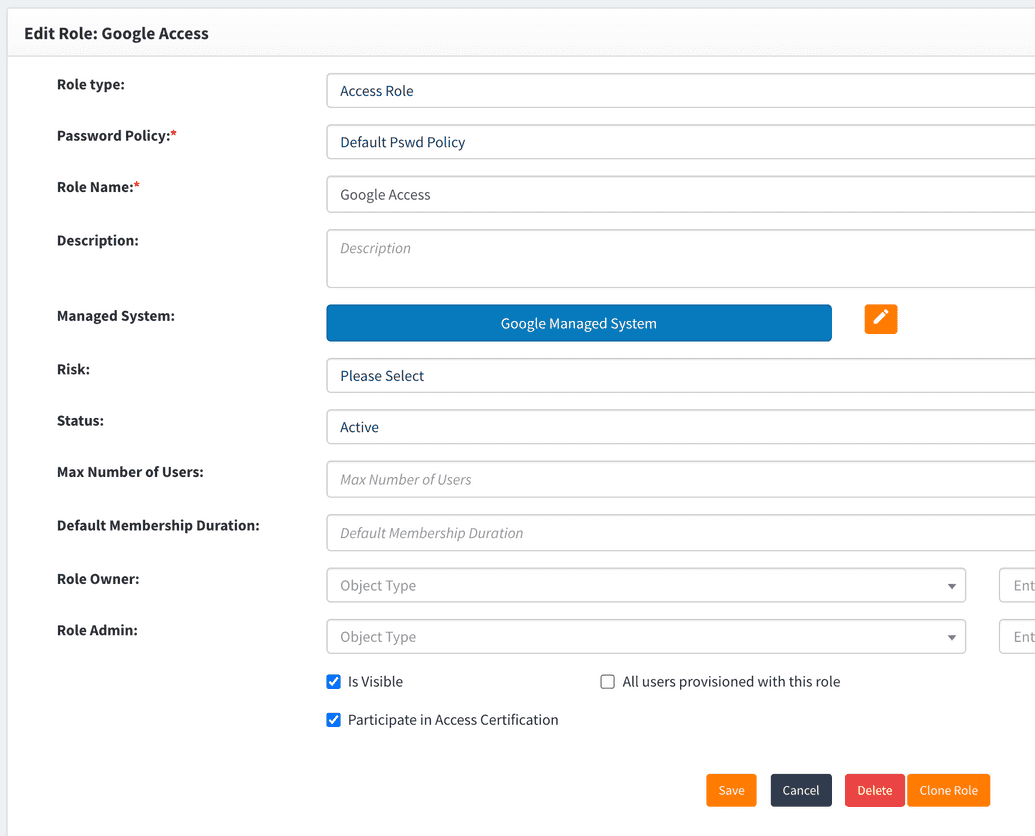
Create access role for Google Managed System.
The OpenIAM identity manager allows you to provision users based on a user's role membership. You can choose between role-based provisioning, rules-based provisioning, or both.
The association between a resource and a role determines the systems that a user is provisioned into or to which they are granted access.
Therefore, for role-based provisioning to work, you need to first associate resources to a role. This means that when a user is a member of a role, they are provisioned into those resources.
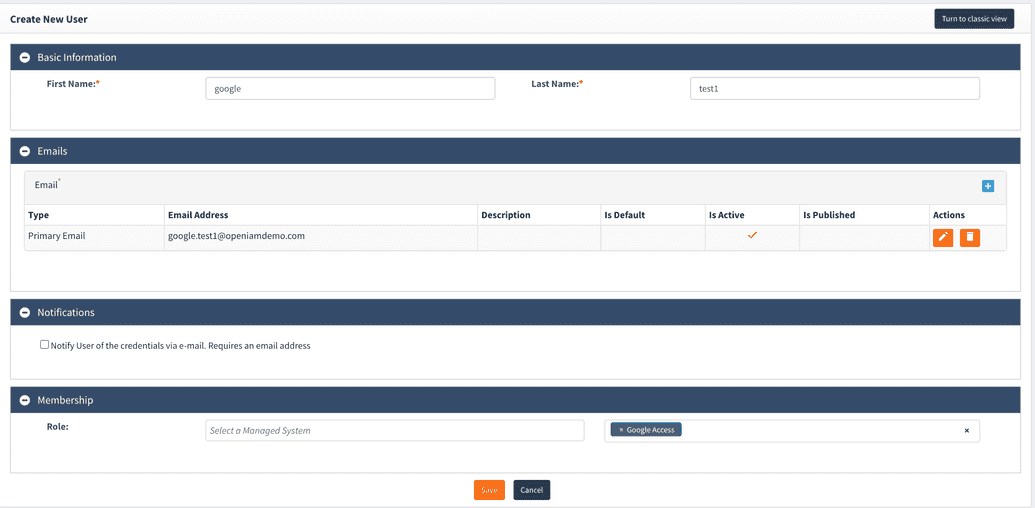
Create New User and provision to Google
Webconsole → User Admin → Create New User. If you would like to provision user to Google you need to add this user to role that associate with google managed system
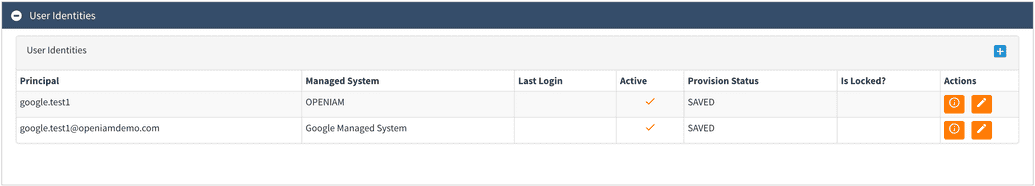
To check if user has been created you can check User Identities and Managed System Dashboard
Synchronization from Google (Sample Example)
Synchronization allows you to synchronize data from one or more authoritative sources to a set of managed systems. Synchronization configuration enables monitoring a source system for changes and then updating target systems at scheduled periodic intervals.
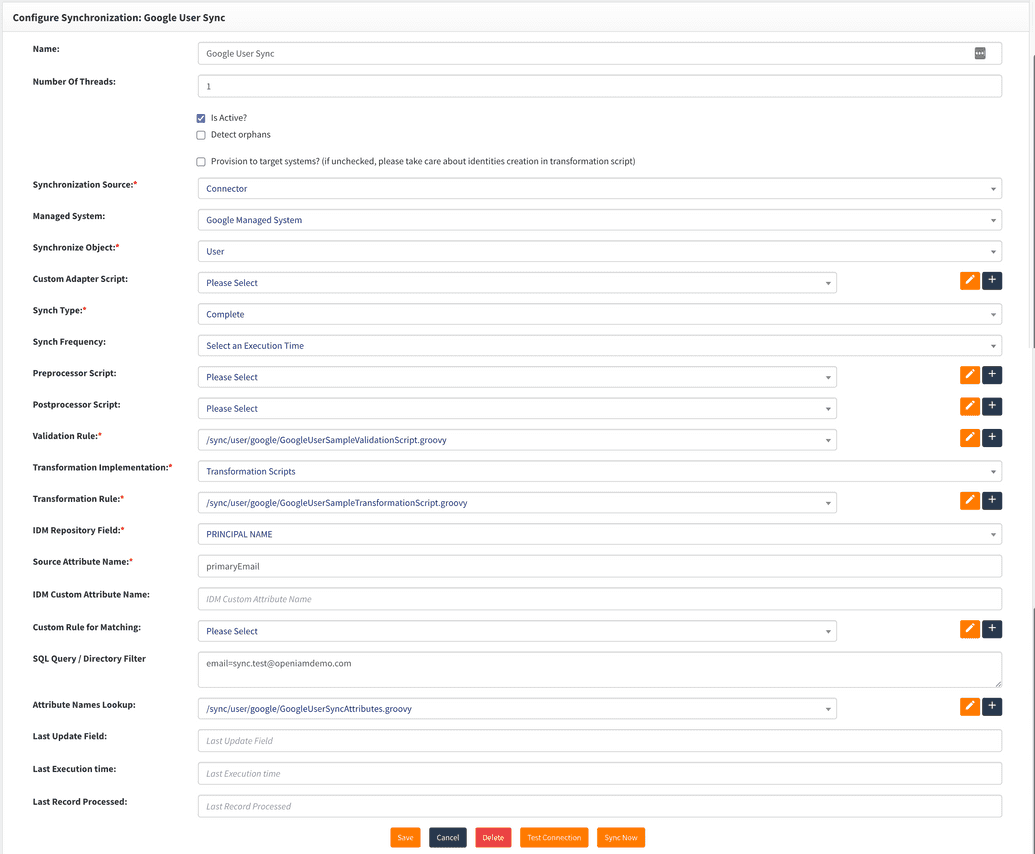
To manage synchronization, Webconsole → click on the Provisioning tab and select Synchronization.
Create New Sync from Google
Sync Now → Will synchronize users from Google to OpenIAM based on provided SQL Query / Directory Filter
See for reference https://developers.google.com/admin-sdk/directory/v1/guides/search-users