Password Policy
The password policy controls the following:
- Password composition.
- Frequency of change.
- SelfService forgot password configuration.
The sections below describe how to configure the password policy. To access the password policy configuration page, go to Policy > Password Policy. If you are new to OpenIAM, start by configuring the existing Default Password Policy instead of creating a new one.
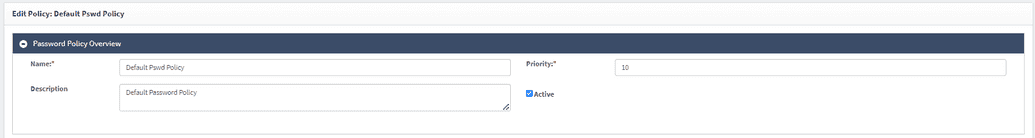
Password Policy Overview
The general data of the password policy contains the following fields:
- Name
- Description
- Priority: A numeric value representing the priority of this policy. A higher number indicates a higher priority over policies with a lower number.
- Active/Not Active flag: If the policy is not active, it won't be used during the policy resolving process.
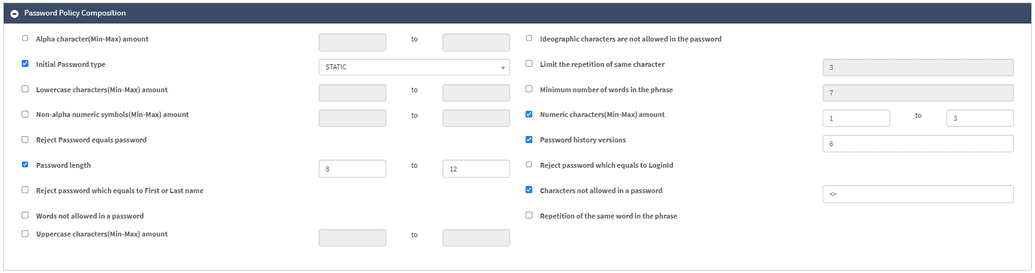
Password Policy Composition
This section of the page allows configuring the details of the required password composition. The description of each field is provided in the table below.
| Field | Description |
|---|---|
| Alpha Character (Min-Max) Amount | Minimum and maximum number of alphabetic (letter) characters that must be included in a password. |
| Ideographic Characters (Chars) Are Not Allowed in the Password | Determines whether it is possible to use CJKV (Chinese, Japanese, Korean, and Vietnamese) ideograph characters defined by the Unicode Standard. |
| deprecated Initial Password Type | Random vs static password generation must be defined in OPENIAM managed system policy map -> password groovy script. Example of random groovy password you can find in Appendix below. |
| Limit the Repetition of the Same Character | For example, if this value is set to 3, then the password kkfd44kddsk is not acceptable since it contains four 'k' letters, but kkfd44Kddsk will be accepted since one 'K' is uppercase. |
| Lowercase Characters (Min-Max) Amount | Minimum and maximum number of lowercase (small) characters that must be included in a password. |
| Minimum Number of Words in the Phrase | Specifies the least number of words a passphrase or password phrase must contain. |
| Non-alpha Numeric Symbols (Min-Max) Amount | The minimum and maximum number of non-alphanumeric symbols (punctuation marks, special symbols, and other characters) that must be included in a password. |
| Numeric Characters (Min-Max) Amount | The minimum and maximum number of numeric (digit) characters that must be included in a password. |
| Reject Password Equals Password | If this is checked, the policy forbids the password to be the word "password". |
| Password History Versions | Feature implemented in systems to track and manage the historical passwords associated with a user account. It's a numerical value. |
| Password Length | Determines the length of the password. |
| Reject Password Which Equals to LoginId | If this is checked, the policy forbids the password to be the same as "LoginId". |
| Reject Password Which Equals to First or Last Name | If this is checked, the policy forbids the password to be the same as the first or last name of a user. |
| Characters Not Allowed in a Password | Specifies certain characters that users are prohibited from including in their passwords. |
| Words Not Allowed in a Password | If the password is in the blacklist (password dictionary), it will be rejected. To add a password dictionary, check the box and go to the Import/Export section at the very end of the page. Add the file with the dictionary to the Upload Password Dictionary field by clicking Browse. |
| Repetition of the Same Word in the Phrase | If checked, prevents users from using identical or repeated words within the same passphrase. |
| Uppercase Characters (Min-Max) Amount | Minimum and maximum number of uppercase (capital) characters that must be included in a password. |
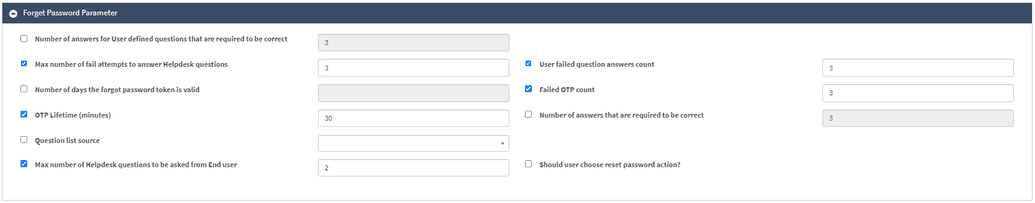
Forgot Password Parameter
This section of the page allows configuring the details of the forgot password parameters and steps to restore it. The description of the fields is given in the table below.
| Field | Description |
|---|---|
| Number of Answers for User Defined Questions That Are Required to Be Correct | OpenIAM provides 18 out-of-the-box security questions but also allows the creation of custom questions. To use this function via the web console, go to Administration > Challenge Response Questions > Create New Question. If you have custom questions, this policy defines the number of correct answers. This can also be done via the SelfService portal; the steps are described in the document by this link. |
| Max Number of Fail Attempts to Answer Helpdesk Questions | See Helpdesk protection for more information. |
| User Failed Question Answers Count | Each time the user answers a question incorrectly, their failure count will increase. Upon surpassing the set number, the account will be locked. |
| Number of Days the Forgot Password Token Is Valid | If not set, the default value is 3. Note: The values can only be set for days, with a minimum value of 1. |
| Failed OTP Count | The number of unsuccessful attempts to enter or verify a One-Time Password (OTP). If not set, the default value is 3. |
| OTP Lifetime (Minutes) | The duration of time during which a One-Time Password (OTP) is valid for authentication. The default value is 30 minutes. |
| Number of Answers That Are Required to Be Correct | The minimum number of correct answers needed for out-of-the-box security questions. |
| Number of Questions to Display | The total number of questions to be asked. |
| Question List Source | The source of Security questions is taken from. |
| Max Number of Helpdesk Questions to Be Asked to the End User | See Helpdesk protection for more information. |
| Should User Choose Reset Password Action? | If checked, the decision to reset the password is taken by the user. |
To disable security questions so that they won't be displayed during the first login, disable the following policies:
- Max number of fail attempts to answer Helpdesk questions.
- Number of answers that are required to be correct.
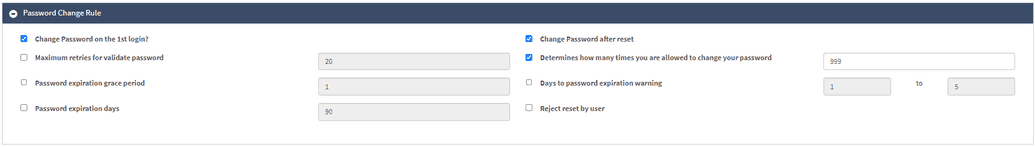
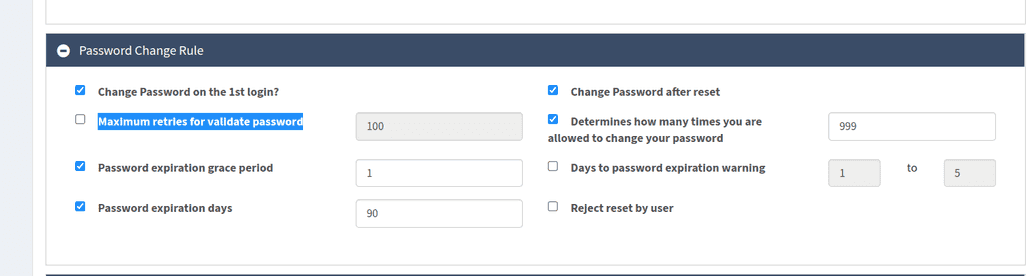
Password Change Rule
This section of the page allows configuring the details of changing the password. The description of the fields is given in a table below.
| Field | Description |
|---|---|
| Change Password on the 1st Login? | If checked, then the user is required to change the initial password upon the first login. |
| Maximum retries for validate password | Number of attempts to validate password. |
| Password expiration grace period | The number of days after the password has expired during which the user is permitted to continue to log in. |
| Password expiration days | Number of days the password stays valid and active. Note: If your goal is to establish a password policy that ensures users' passwords never expire, this can be achieved by populating the field with larger number like 9999. Currently, there is no way to allow a password not to expire without setting the password expiration in above mentioned way. |
| Change Password after reset | This requires the user to change his/her password after the administrator resets the password for the user. |
| Determines How Many Times You Are Allowed to Change Your Password | A numerical value counting the time the user is allowed to change the password. |
| Days to password expiration warning | A numerical value meaning the number of days prior expiration, when the user is sent a warning. |
| Reject reset by user | If checked, the password reset by the user will be rejected. |
There is also a possibility to limit password validation attempts. Here, after the limit is reached, an error will be thrown:
Maximum limit for password validation for an identity reached.
User will again be able to validate this password after 10 minutes.
Note: On the 1st login, the user might be directly taken to challenge questions after entering the password on login, instead of being asked to change their password. This event might happen even if Change Password on the 1st Login? field is checked. To tackle this issue, make sure to set the PENDING_INITIAL_LOGIN status in the sync script for new users.
Multiple password policies
OpenIAM provides the capability to link multiple password policies to various objects such as roles, groups, organizations, managed systems and authentication policies. When a user sets/resets a password, a password policy resolver is called. The password policy with the highest priority is then applied.
Example:
- There are several password policies in OpenIAM: The Default Password Policy with a priority of 10; CustomPolicy1 with a priority of 14 (more restricted than the default password policy); _AD Password Policy_with a priority of 15.
- The following objects are in OpenIAM: The role Manager is linked to CustomPolicy1; the group AD Users is linked to AD Password Policy; the organization Sales Department is linked to Default Password Policy.
- The user John.Snow has a Manager role and is a member of the Sales Department organization.
- The user Sansa.Stark belongs to the AD Users group and is a member of the Sales Department organization.
- The user Arya.Stark has a Manager role and belongs to the AD Users group.
Appendix 1
Groovy script to generate random password
package org.openiamimport org.openiam.api.connector.groovy.AbstractIPolicyMapGroovyimport org.openiam.api.connector.model.ConnectorAttributeimport org.openiam.api.connector.model.StringOperationalConnectorValueimport org.openiam.base.AttributeOperationEnumimport org.openiam.base.response.list.PolicyListResponseimport org.openiam.common.beans.mq.PolicyRabbitMQServiceimport org.openiam.idm.provisioning.diff.model.user.ProvisionUserObjectDiffimport org.openiam.idm.searchbeans.PolicySearchBeanimport org.openiam.idm.srvc.pswd.service.PasswordGeneratorimport org.springframework.beans.factory.annotation.Autowired/*** Script generates random password using password policy*/class UserPassword extends AbstractIPolicyMapGroovy<ProvisionUserObjectDiff> {private static final String DEFAULT_POLICY_ID = "4000"@Autowiredprivate PolicyRabbitMQService policyRabbitMQService@Overrideboolean isPerform(ProvisionUserObjectDiff diffObject) {return AttributeOperationEnum.ADD.equals(diffObject.getStatus())}@Overridevoid perform(ConnectorAttribute attribute, ProvisionUserObjectDiff diffObject) {PolicySearchBean psb = new PolicySearchBean()psb.addKey(DEFAULT_POLICY_ID)PolicyListResponse response = policyRabbitMQService.findBeans(psb, 0, 1)String password = PasswordGenerator.generatePassword(response.getList().get(0))attribute.addValue(new StringOperationalConnectorValue(password, diffObject.getStatus()))}}