OpenID Connect
OpenID Connect (OIDC) is a simple identity layer on top of the OAuth 2.0 protocol. It allows clients to verify the identity of the end-user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner.
OpenID Connect allows a variety of clients, including web, mobile, and JavaScript clients, to request and receive information about authenticated sessions and end-users. The specification is extensible and allows participants to use optional features such as encryption, identity data, discovery of OpenID Providers, and session management.
The example below shows how to integrate an Angular app with OpenIAM using OIDC. However, you can leverage the steps described below to integrate your OIDC application with OpenIAM.
Create an Authentication Provider
To create a new authentication provider:
- Log in to the web console and go to Access Control > Authentication Provider
- Go to
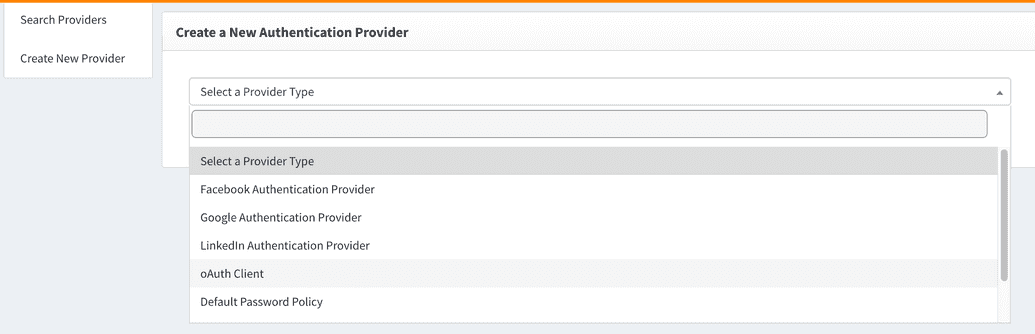
Create New Provider - Since OIDC is a layer on top of OAuth, OpenIAM combines the UI to configure both OAuth and OIDC clients. Please select
OAuth Clientfrom the "Select a Provider Type" dropdown as shown below
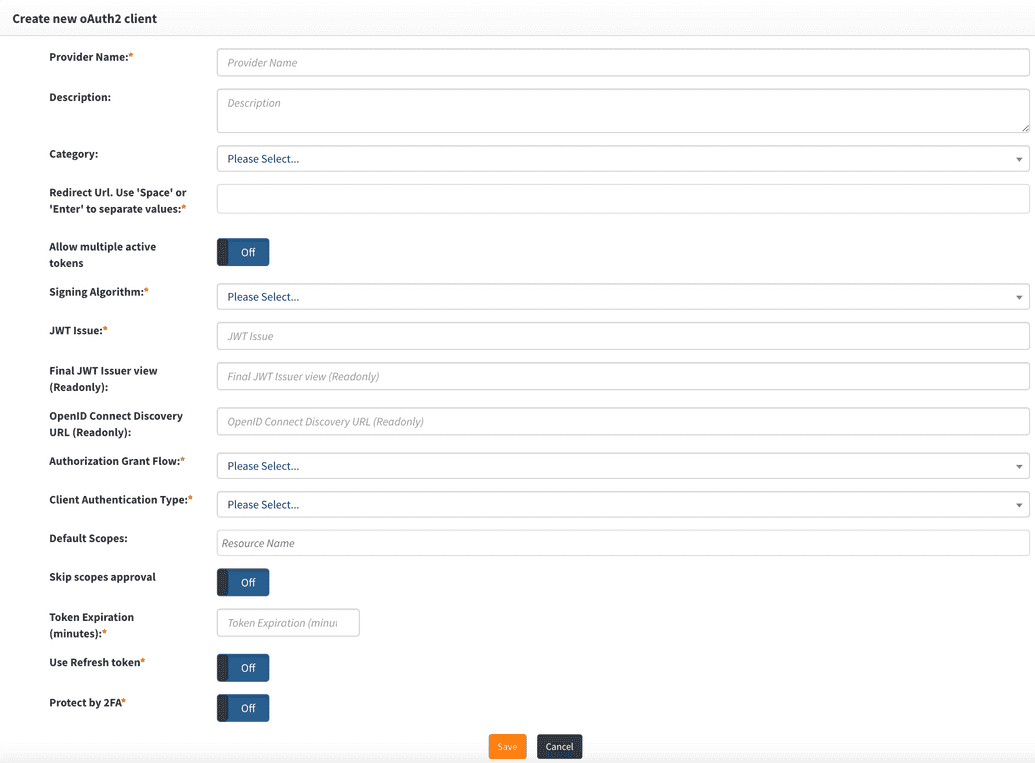
Configure OIDC Client Provider in OpenIAM
| Field Name | Description |
|---|---|
| Provider name | This can be any descriptive name to identify this configuration, such as angular-oidc-app |
| Redirect URL | Redirect URLs are a critical part of the OAuth flow. After a user successfully authorizes an application, the authorization server will redirect the user back to the application with either an authorization code or access token in the URL. Since the redirect URL can contain sensitive information, it is critical that the service doesn’t redirect the user to an arbitrary location. |
| Allow multiple Active Tokens | Set this value to Off, which is the default. |
| Signing Algorithm | Select the algorithm used to sign tokens issued for your application or API. An example is RS-256. |
| JWT Issuer | This is the JWT issuer. It identifies the client that will be issued the JWT token. In this case, you can put any descriptive value like angular-oidc-app. |
| Final JWT Issuer view | This value will be automatically generated upon completing the "JWT Issuer" value. |
| OpenID Connect Discovery URL | This value will be automatically generated upon completing the "JWT Issuer" value. You can configure your OIDC application using the information found at the URL. |
| Authorization Grant Flow | The grant flow dropdown requires the selection of a grant type. The grant describes how the client application acquires an access token that can be used to authenticate a request to an API endpoint. Note: The grant type that you select here must align with the grant flow that you define in your application. For this example, select Implicit from the dropdown. |
| Client Authentication Type | Describes how credentials are passed to the authorization server. You can select between Basic Authentication and Request Body. For this example, select Request Body. |
| Default Scopes | Scopes in OAuth 2.0 provide a way to limit the amount of access that is granted to an access token. You can select the scopes from the dropdown. Note that scopes in OpenIAM are resources, and you can manage them through the Resource Manager interface described under Access control. |
| Skip scope approval | Set this to Off. |
| Token expiration | Access tokens expire after the specified minutes of being idle. You can set this value to 30 minutes. |
| Use refresh token | Refresh tokens carry the information necessary to get a new access token. Whenever an access token is required to access a specific resource, a client may use a refresh token to get a new access token issued by the authentication server. In most cases, this value should be set to Off. |
| Protect by 2FA | Set this value to Off unless you want to use 2FA during the authentication process. |
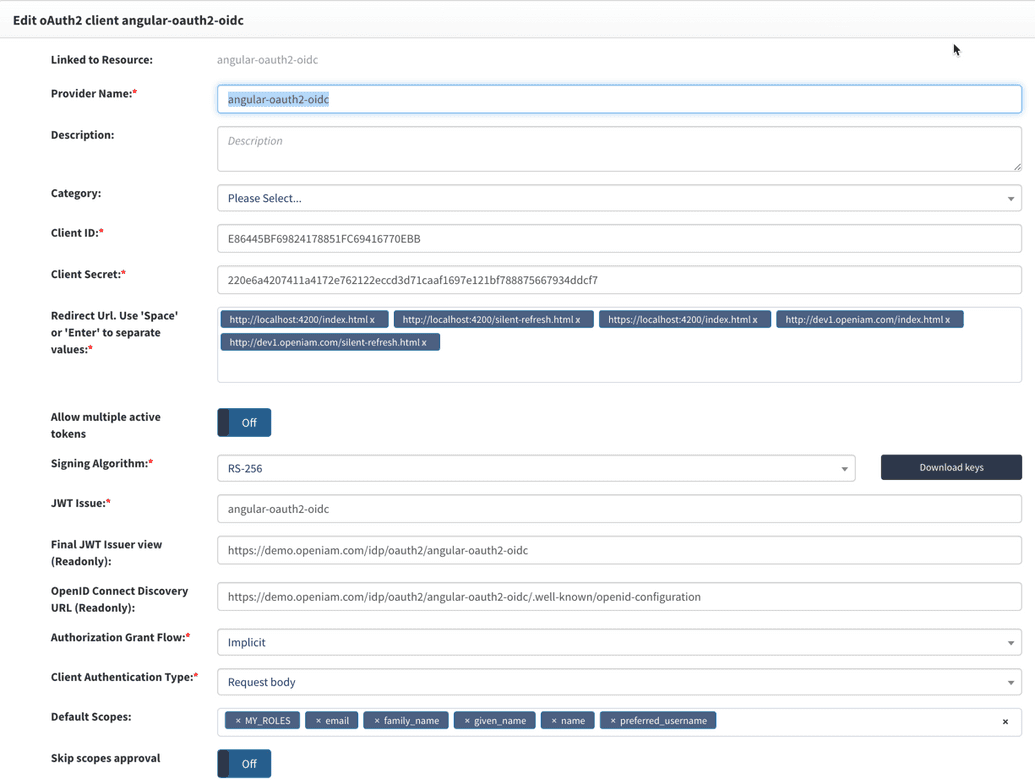
The example represents a valid authentication provider configuration for use with the test Spring Boot application that was referenced earlier in this section.
Upon saving the configuration, the system will generate the clientid and clientsecret, which will be used by your OAuth client.
Grant access to your application
To access the service provider through the IdP, we must grant access to the service provider by associating it with an entitlement object such as a group or role. While this topic is described in detail in the access control section, the section below provides a brief reference to entitle an application through a role.
- Go to the Webconsole -> Access Control -> Role
- Find an existing role that you want to update to be entitled to your service provider
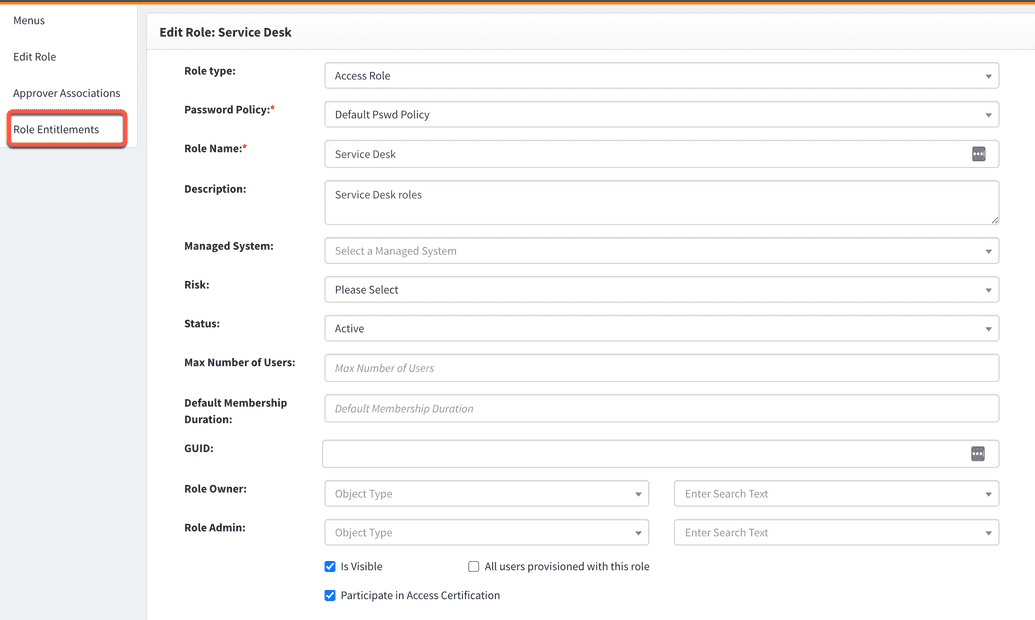
- View the role details by clicking on the icon in the Actions column
- Go to the
Role Entitlementsoption from the side menu as shown below
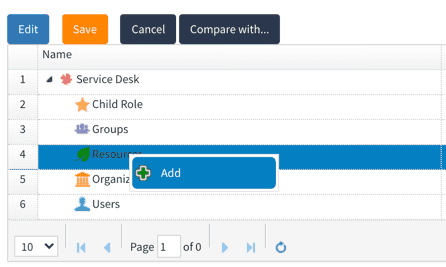
- Right-click on
Resourcefollowed by selectingAddas shown below
- From the
Resource typedropdown, selectAuthentication provider - From the adjacent dropdown, select the name of your authentication provider as shown below
The role has now been entitled.
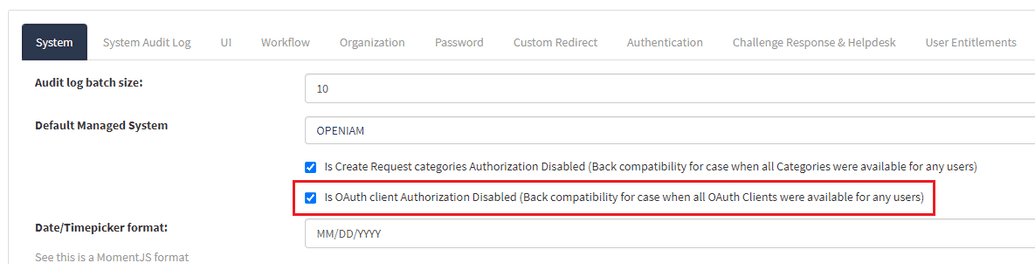
Note: Make sure to enable the Is OAuth client Authorization Disabled (Back compatibility for cases when all OAuth Clients were available for any users) checkbox. If not checked, the user entitlements will not be connected to the resource and the role entitled to the authentication provider will not work.
To check the required checkbox, go to web console > Administration > System configuration > System tab.
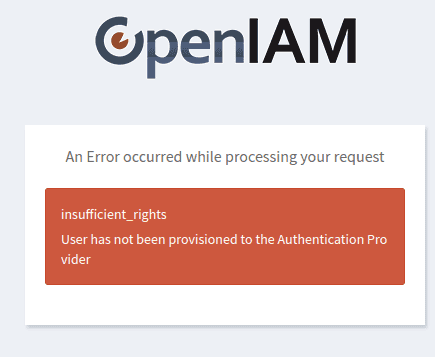
If the checkbox is disabled, a user without entitlements to the OAuth authentication provider will get an insufficient_rights message on login, as shown below.