Authentication
The authentication framework in OpenIAM provides a flexible solution where you can configure a variety of parameters to implement a flexible and secure authentication solution. This section describes the authentication functionality found in OpenIAM and how it can be configured.
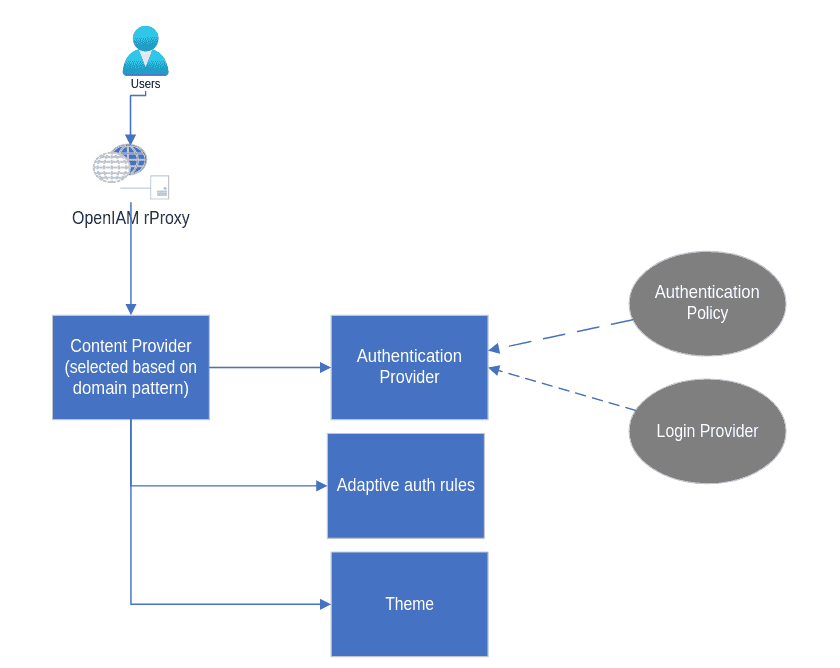
The framework consist of several components which are described below:
- Authentication policy - Used to define authentication parameters such as failed authentication attempts, token life, auto-unlock,etc.
- Authentication provider - Defines the type of authentication which will be used; UserID/password, OTP, Certificate, etc.
- Adaptive authentication provider - Allows for the creation of authentication workflows which take into account other factors such as IP address, Role, etc.
- Content provider - Enables the association of an authentication provider to a domain or URL
The diagram above describes how the various parts of the authentication framework fit together.
Configuring Authentication Overview
The tutorial for configuring authentication start with the simple example which is then expanded to cover other types of authentication. The progression of the tutorial is described below:
- Configure authentication
- Password based authentication
- Directory based authentication
- Strong authentication using OTP
- Step-up authentication
Once you are familiar with the framework, you can extend your authentication model by leveraging the authentication methods described below.
Authentication Methods
OpenIAM supports the authentication methods described below
| Name | Description |
|---|---|
| SMS / E-mail OTP | Users log in OpenIAM using an OTP over SMS or e-mail. |
| Password authentication | Users authenticate into OpenIAM using a userId and password. |
| Social media authentication | Users log in OpenIAM using their social identity |
| Adaptive authentication | Adaptive authentication configuring to create robust authentication flows |
| Authentication using a FIDO2 device | Users use FIDO 2 to authenticate into OpenIAM |
| Credential provider | Credential provider for Mac and Windows to replace the OS authentication interface. |
| Delegated Authentication | Describes how to configure an external repository (Managed System) for authentication. Managed system based authentication allows customers to use Directories such as LDAP and Active Directory and other for authentication. |
| Certificate Based Authentication | Describes configuring Certificate Based Authentication in OpenIAM |
| Authenication via Criipto | Decribes how to configure authentication process via Criipto. |