Adaptive Authentication
The Adaptive Authentication functionality in OpenIAM allows organizations to create authentication flows which go beyond direct authentication options such as password, OTP, certificate, etc. These flows can be used to evaluate other factors such as IP address, Role, etc. during the authentication process.
Authentication rules
Authentication rules are policies and guidelines that define how users or systems verify their identities before accessing resources, applications, or services. These rules ensure that only authorized users gain access and help protect sensitive data from unauthorized access.
This can be the length and composition of a password or user ID for user ID and password authentication, requiring multiple authentication factors for MFA, restricting login attempts for time-based authentication, etc. OpenIAM allows configuring the authentication rules to suit you business purposes, as defined below.
Configuring authentication rules
- Go to webconsole > Policy > Authentication Rule.
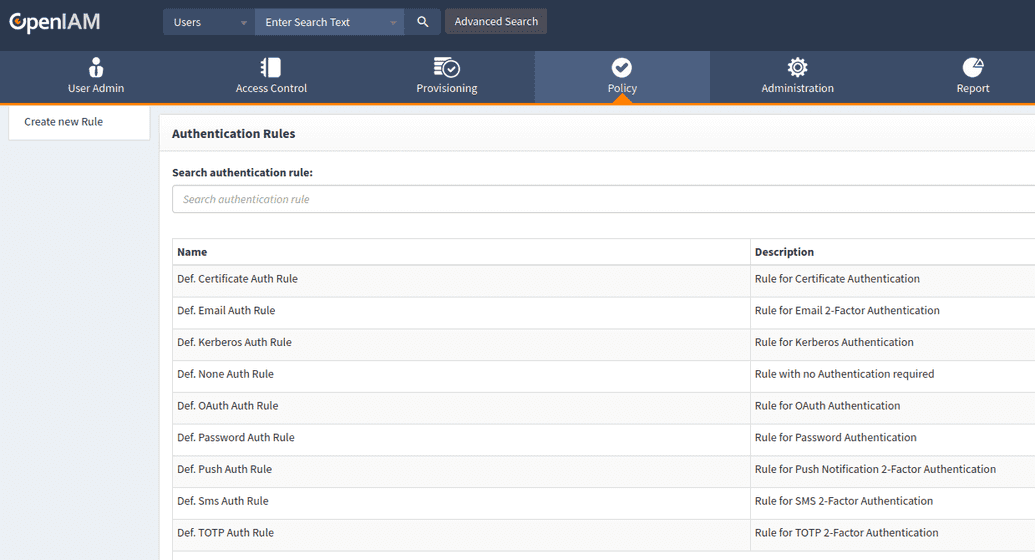
List of default authentication rules consist of rules for each type of authentication
One-step authentication
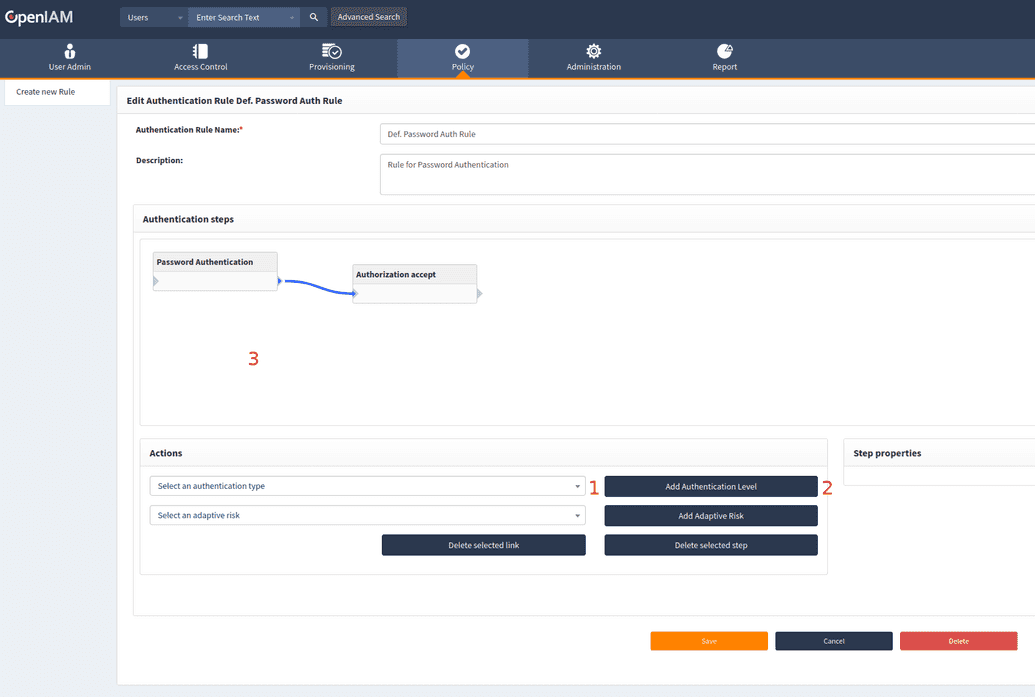
All default authentication rules are true for one type of authentication. To add authentication type into a rule field, follow the steps below.
- Select authentication type from list of types.
- Push the Add Authentication Level button.
- Authentication type will be added into the rule field.
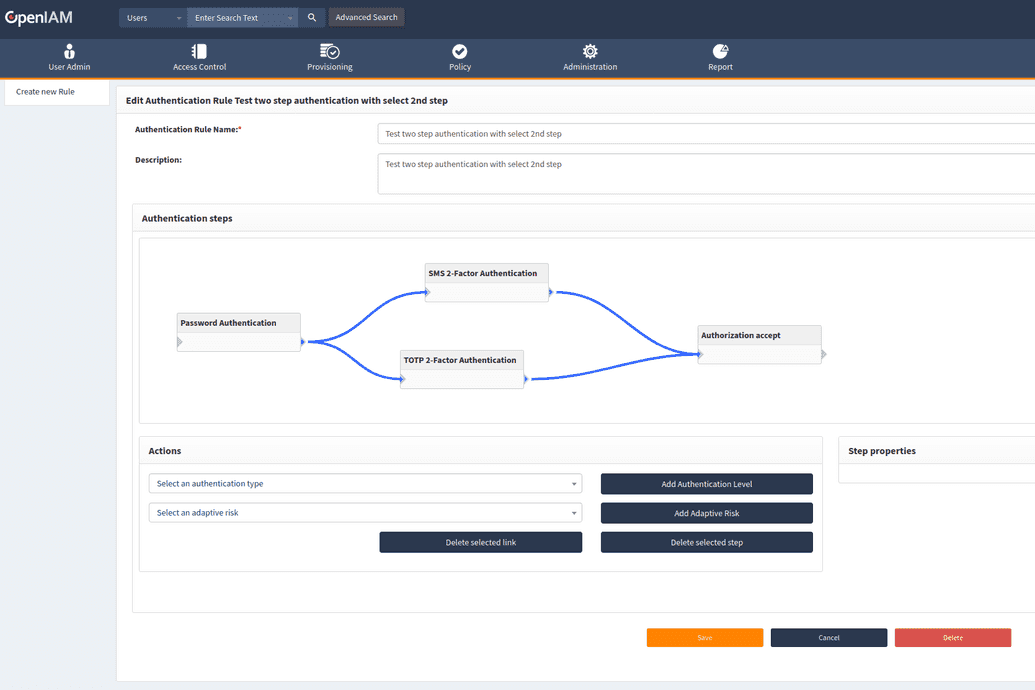
Two or more steps authentication
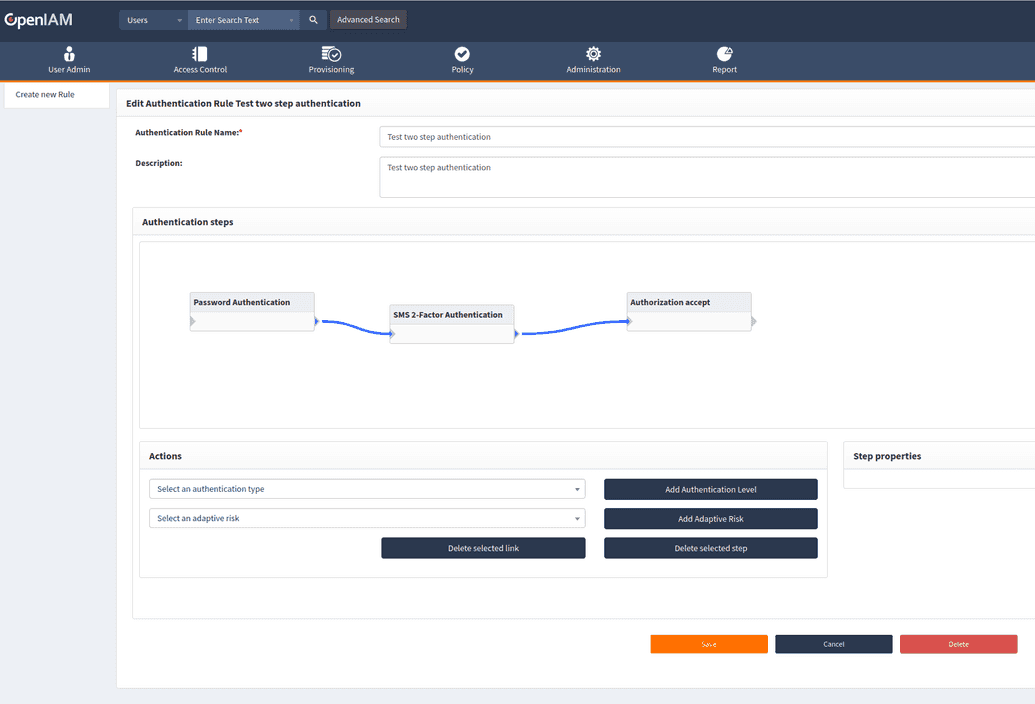
In case you opt for having more than one step of authentication, you will need to configure not only the authentication steps for each type, but also their order. You can configure those using the instructions below.
- Select authentication type from list of types.
- Push the Add Authentication Level button.
- Authentication type will be added into the rule field.
- If needed, repeat the steps starting from step 1.
- Using a mouse cursor add link between authentication types.
Selecting one authentication type from list of allowed
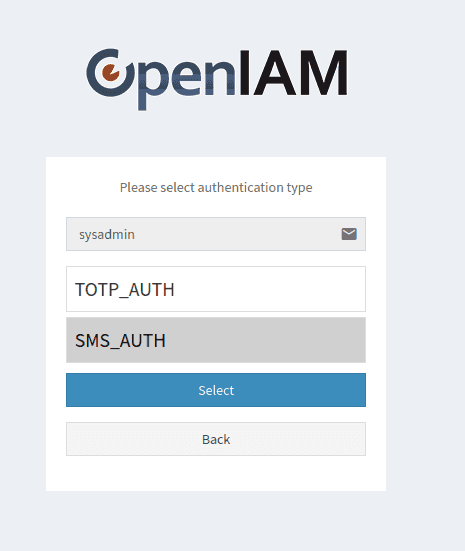
In case you have several authentication types available, you can allow several types. However, to do that, you have to use next authentication rule type.
In this case, after success login with password, user will be redirected to a selecting page with authentication types list.
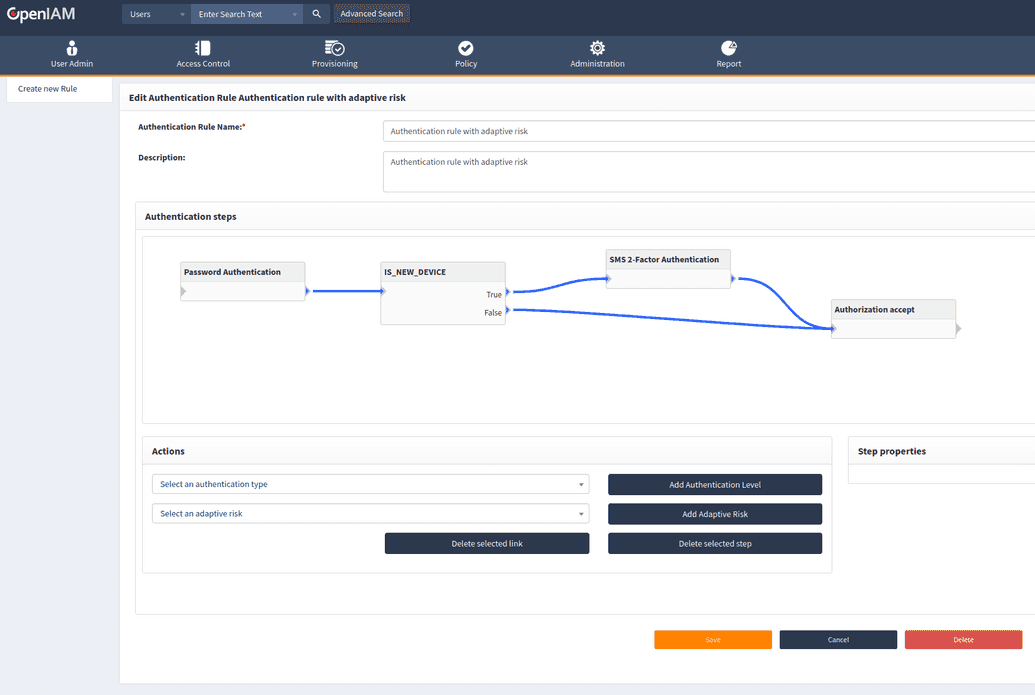
Authentication rule with adaptive authentication
According to the situation there may be a need to use an extra authentication step or to decline access. For this purpose, you can use adaptive risks when creating an authentication rule.
For example, you may include an extra authentication step if a user uses a new device on login, as describe in a screenshot below.
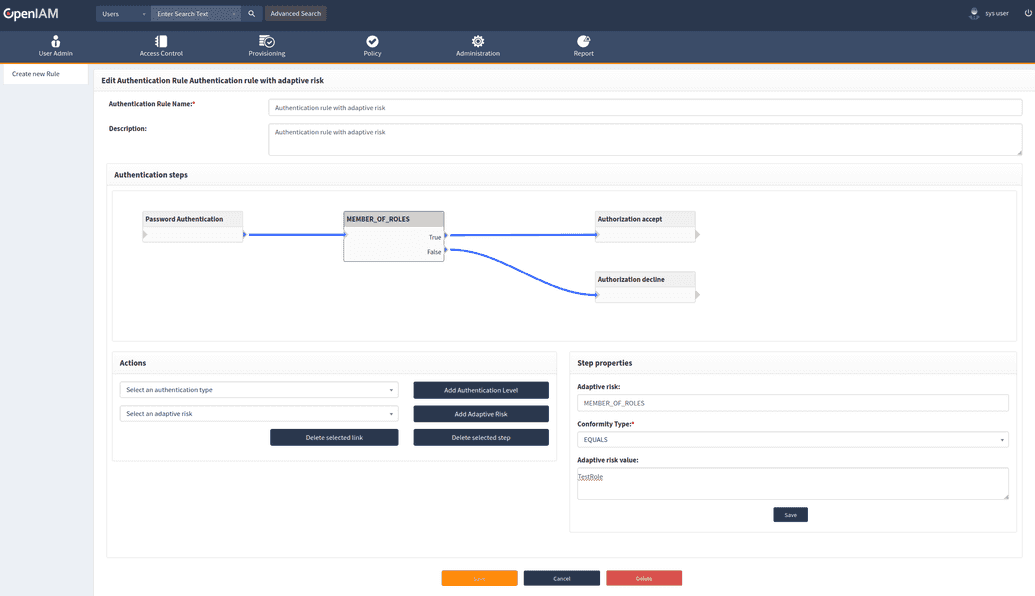
Another example is accepting access for a selected role.
Adaptive risks
All adaptive risks have a true or false resulting value. Next step of adding an authentication rule is to calculate the risk result. There are two types of adaptive risks - IS_NEW and other.
ISNEW.... adaptive risk needs no additional value in Adaptive risk value field. It may be:
IS_NEW_IP.IS_NEW_DEVICE.FORGOT_PHONE.IS_NEW_CITY(this risk is allowed if a DB used has a geolocation by IP address).IS_NEW_COUNTRY(this risk is allowed if a DB used has a geolocation by IP address).
The Other type of adaptive risks use value from Adaptive risk value field and calculate result. These are:
MEMBER_OF_ROLES.MEMBER_OF_GROUPS.HAS_APPROVED_AUTH_TYPE.CUSTOM_ADAPTIVE_RISK.