Password update for OpenIAM services in Kubernetes
Redis passwords
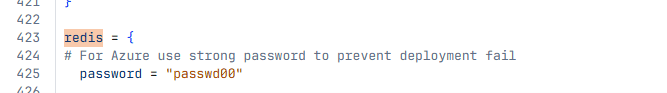
- Update the default Redis password in
terraform.tfvars.
vi terraform.tfvars
Here, locate the Redis password variable and update it.
- Take a backup of the existing Kubernetes secret and verify current password in secret.
kubectl -n default get secret secrets -o yaml > ~/secrets.defaults.backup.yamlkubectl -n default get secret secrets -o jsonpath='{.data.redisPassword}' | base64 --decode && echokubectl -n default get secret secrets -o jsonpath='{.data.redisSentinelPassword}' | base64 --decode && echo
- Uninstall Redis via Helm and remove its resources from the Terraform state.
root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep redistest2025-redis default 2 2025-10- 14 14:45:41.873592306 +0000 UTC deployed redis-18.17.0 7.2.4root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-redisrelease "test2025-redis" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep redisroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list| grep redismodule.deployment.module.redis.helm_release.redismodule.deployment.module.redis.null_resource.depends_onroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.redis.helm_release.redisRemoved module.deployment.module.redis.helm_release.redisSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.redis.null_resource.depends_onRemoved module.deployment.module.redis.null_resource.depends_onSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list| grep redisroot@ubuntu-test:~/kubernetes-docker-configuration#
- Verify the installed ConfigMap that contains the secret intended for injection into pods, and then delete it.
root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configtest2025-configmap default 3 2025-10-14 14:45:39.681903426 +0000 UTC deployed openiam-configmap-4.2.1-12 1.0root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-configmaprelease "test2025-configmap" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configmodule.deployment.module.helm.helm_release.configmaproot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.helm.helm_release.configmapRemoved module.deployment.module.helm.helm_release.configmapSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#
- Delete vault bootstrap job.
root@kube-access:~# kubectl get jobs| grep boottest2025-vault-bootstrap-job Complete 1/1 2m13s 39mroot@kube-access:~#kubectl delete job test2025-vault-bootstrap-job
- Apply terraform using the command below.
terraform apply --auto-approve
- Monitor the status of the pods.
kubectl get pods
Once all pods are up and running, log in to the webconsole and verify that all services are functioning correctly.
Note: The above steps have been prepared assuming the namespace is default.
If any pod remains in a 0/1 state, delete it using the command below.
If any pod remains in a 0/1 state, delete it using the command below.
kubectl delete pod <pod-name>
Elasticsearch passwords
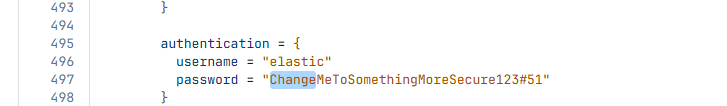
- Update the default Elasticsearch password in
terraform.tfvars.
vi terraform.tfvars
Locate the ElasticSearch password variable and update it.
- Take a backup of the existing Kubernetes secret and verify current password in secret.
kubectl -n default get secret secrets -o yaml > ~/secrets.defaults.backup.yamlkubectl -n default get secret secrets -o jsonpath='{.data.elasticsearchUserName}' | base64 --decode && echokubectl -n default get secret secrets -o jsonpath='{.data.elasticsearchPassword}' | base64 --decode && echo
- Update the Elasticsearch password in the Elasticsearch pod with the new value. Log in to the Elasticsearch pod and verify the current cluster health using the existing password.
kubectl get pods | grep elaskubectl exec -it elasticsearch-master-0 shcurl -u elastic:ChangeMeToSomethingMoreSecure123#51 -X GET "http://localhost:9200/_cluster/health?pretty"
Replace the old and new passwords in the following command to update Elasticsearch with the new password.
curl -u "elastic:Oldpassword" -XPOST -H "Content-Type: application/json" \"http://localhost:9200/_security/user/elastic/_password" \-d '{ "password": "NEWPASSWORD" }'
Verify that the new password is working using the following command.
curl -u elastic:ChangeMeToSomethingMoreSecure123#51 -X GET "http://localhost:9200/_cluster/health?pretty"
- Uninstall Elasticsearch via Helm and remove its resources from the Terraform state.
helm ls | grep elashelm delete test2025-elasticsearchroot@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep elastest2025-elasticsearch default 1 2025-10-14 08:39:01.24106775 +0000 UTC deployed elasticsearch-7.17.3 7.17.3root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-elasticsearchrelease "test2025-elasticsearch" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep elasmodule.deployment.module.elasticsearch.helm_release.elasticsearchmodule.deployment.module.elasticsearch.null_resource.depends_onroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.elasticsearch.helm_release.elasticsearchRemoved module.deployment.module.elasticsearch.helm_release.elasticsearchSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.elasticsearch.null_resource.depends_onRemoved module.deployment.module.elasticsearch.null_resource.depends_onSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep elasroot@ubuntu-test:~/kubernetes-docker-configuration#
- Verify the installed ConfigMap that contains the secret intended for injection into pods, and then delete it.
root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configtest2025-configmap default 3 2025-10-14 14:45:39.681903426 +0000 UTC deployed openiam-configmap-4.2.1-12 1.0root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-configmaprelease "test2025-configmap" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configmodule.deployment.module.helm.helm_release.configmaproot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.helm.helm_release.configmapRemoved module.deployment.module.helm.helm_release.configmapSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#
- Delete vault bootstrap job.
root@kube-access:~# kubectl get jobs| grep boottest2025-vault-bootstrap-job Complete 1/1 2m13s 39mroot@kube-access:~#kubectl delete job test2025-vault-bootstrap-job
- Apply terraform using the command below.
terraform apply --auto-approve
- Monitor the status of the pods.
kubectl get pods
- Once all pods are up and running, log in to the webconsole and verify that all services are functioning correctly.
Note: The above steps have been prepared assuming the namespace is default.
If any pod remains in a 0/1 state, delete it using the command below.
If any pod remains in a 0/1 state, delete it using the command below.
kubectl delete pod <pod-name>
RabbitMQ passwords
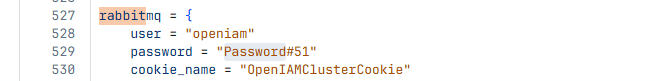
- Update the default RabbitMQ password in
terraform.tfvars.
vi terraform.tfvars
Locate the RabbitMQ password variable and update it.
- Take a backup of the existing Kubernetes secret and verify current password in secret.
kubectl -n default get secret secrets -o yaml > ~/secrets.defaults1.backup.yamlkubectl -n default get secret secrets -o jsonpath='{.data.rabbitmqPassword}' | base64 --decode && echo
- Uninstall RabbitMQ via Helm and remove its resources from the Terraform state.
root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep rabbittest2025-rabbitmq default 1 2025-10- 14 14:20:17.981710745 +0000 UTC deployed rabbitmq-10.1.16root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-rabbitmqrelease "test2025-rabbitmq" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep rabbitroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep -i rabbitmodule.deployment.module.helm.helm_release.rabbitmqroot@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.helm.helm_release.rabbitmqRemoved module.deployment.module.helm.helm_release.rabbitmqSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep -i rabbitroot@ubuntu-test:~/kubernetes-docker-configuration#Delete the PVC of the RabbitMQ pod and verify that the corresponding PV is automatically deleted.root@ubuntu-test:~/kubernetes-docker-configuration# kubectl get pvc | grep rabbitmqdata-test2025-rabbitmq-0 Bound pvc- f045271d-b685-4c91-9656-3855b5763759 8Gi RWO default <unset> 16hopeniam-pvc-ldap-connector-rabbitmq Bound pvc-25b388f1-6bbe-4c3f-983a-afed2dadcfc0 5M RWX nfs <unset> 3d19hopeniam-pvc-rabbitmq-jks Bound pvc-f05f4ec3-52ae-433a-80cf-9f15a6940905 5M RWX nfs <unset> 3d19hroot@ubuntu-test:~/kubernetes-docker-configuration# kubectl delete pvc data-test2025-rabbitmq-0persistentvolumeclaim "data-test2025-rabbitmq-0" deletedroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# kubectl get pv | grep rabbitmqpvc-25b388f1-6bbe-4c3f-983a-afed2dadcfc0 5M RWX Delete Bound default/openiam-pvc-ldap-connector-rabbitmq nfs <unset> 3d19hpvc-f05f4ec3-52ae-433a-80cf-9f15a6940905 5M RWX Delete Bound default/openiam-pvc-rabbitmq-jks nfs <unset> 3d19hroot@ubuntu-test:~/kubernetes-docker-configuration#
- Verify the installed ConfigMap that contains the secret intended for injection into pods, and then delete it.
root@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configtest2025-configmap default 3 2025-10-14 14:45:39.681903426 +0000 UTC deployed openiam-configmap-4.2.1-12 1.0root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# helm delete test2025-configmaprelease "test2025-configmap" uninstalledroot@ubuntu-test:~/kubernetes-docker-configuration# helm ls | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configmodule.deployment.module.helm.helm_release.configmaproot@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state rm module.deployment.module.helm.helm_release.configmapRemoved module.deployment.module.helm.helm_release.configmapSuccessfully removed 1 resource instance(s).root@ubuntu-test:~/kubernetes-docker-configuration#root@ubuntu-test:~/kubernetes-docker-configuration# terraform state list | grep configroot@ubuntu-test:~/kubernetes-docker-configuration#
- Delete vault bootstrap job
root@kube-access:~# kubectl get jobs| grep boottest2025-vault-bootstrap-job Complete 1/1 2m13s 39mroot@kube-access:~#kubectl delete job test2025-vault-bootstrap-job
- Apply terraform using the command below.
terraform apply --auto-approve
- Monitor the status of the pods.
kubectl get pods
- Once all pods are up and running, log in to the webconsole and verify that all services are functioning correctly.
Note: The above steps have been prepared assuming the namespace is default.
If any pod remains in a 0/1 state, delete it using the command below.
If any pod remains in a 0/1 state, delete it using the command below.
kubectl delete pod <pod-name>