oAuth 2.0
OAuth 2.0 is an industry-standard protocol for authorization. oAuth 2.0 focuses on client developer simplicity while providing specific flows for web applications, mobile devices, and desktop applications.
Overview
OpenIAM supports the following authorization grant types.
| Grant Type | Description |
|---|---|
| Authorization Code | The Authorization Code grant type is used by confidential and public clients to exchange an authorization code for an access token. After the user returns to the client via the redirect URL, the application will get the authorization code from the URL and use it to request an access token. |
| Enterprise customers (4.2.1+) should use PKCE instead. | |
| Client credentials | The Client Credentials grant type is used by clients to obtain an access token outside of the user context. This is typically used by clients to access resources about themselves rather than to access user's resources. |
| Health Level Seven International | SMART App Launch Framework used in healthcare for data exchange. OAuth 2.0 authorization servers are configured to mediate access based on a set of rules configured to enforce institutional policy, which may include requesting end-user authorization. Additional details can be found at: http://www.hl7.org/fhir/smart-app-launch/. |
| Implicit | Simplified OAuth flow previously recommended for native apps and JavaScript apps where the access token is returned immediately without an extra authorization code exchange step. Enterprise customers (4.2.1+) should use PKCE instead. |
Note: OpenIAM 4.2.1.x (Enterprise edition) supports a more extensive list of authorization grant flows
The oAuth 2.0 allows significant flexibility in how applications can be integrated. The example below shows the integration process of a custom SpringBoot Application which uses Authorization Code as the Authorization grant type.
Creating an Authentication Provider
The steps below describe how to integrate the oAuth application with OpenIAM.
To create a new Authentication provider:
- Login to the Webconsole and go to Access Control > Authentication Provider
- Go to Create New Provider.
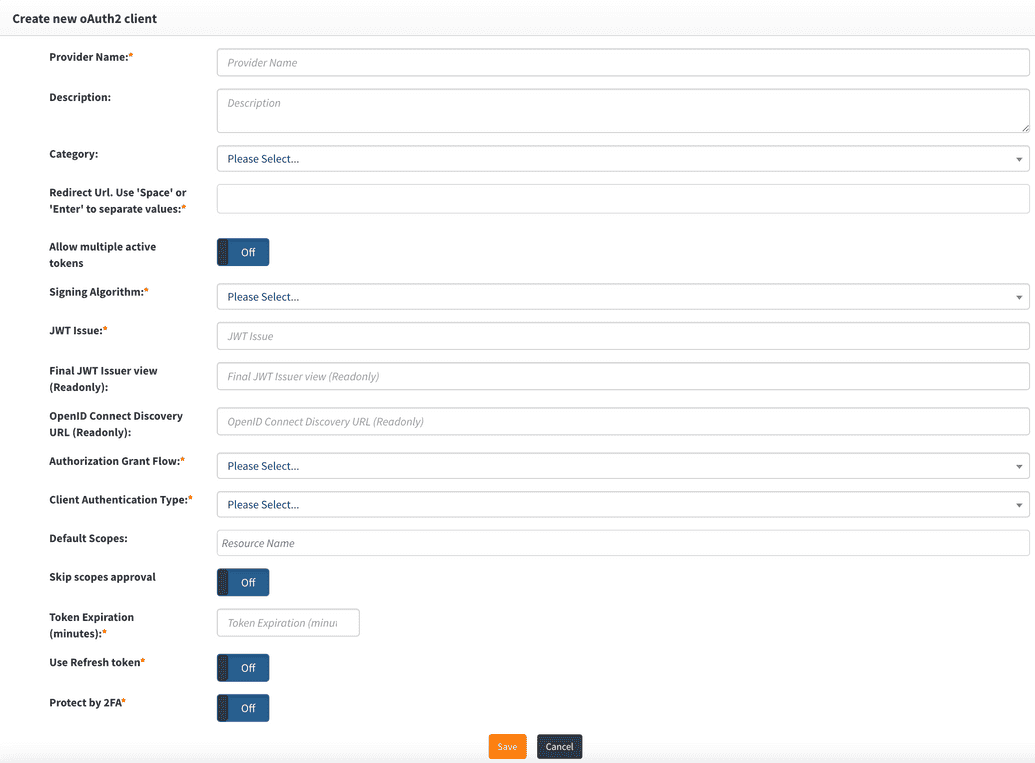
- Select oAuth Client from the Select a Provider Type drop down as shown below.
Configuring the oAuth Client Provider in OpenIAM
| Field Name | Description |
|---|---|
| Provider name | This is any descriptive name to identify this configuration such as OpenIAM OAuth2 with Spring boot. |
| Redirect URL | Redirect URLs are a critical part of the OAuth flow. After a user successfully authorizes an application, the authorization server will redirect the user back to the application with either an authorization code or access token in the URL. Since the redirect URL can contain sensitive information, it is critical that the service doesn't redirect the user to an arbitrary location. |
| Allow multiple Active Tokens | Set this value to Off , which is the default. |
| Signing Algorithm | Select the algorithm used to sign tokens issued for your application or API. Example is RS-256. |
| JWT Issuer | JWT Issuer identifies the client that the JWT token will be issued to. In this case, we can put any descriptive value like openiam-spring-test. |
| Final JWT Issuer view | This value will be automatically generated upon completing the "JWT Issue" value. |
| OpenID Connect Discovery URL | This value will be automatically generated upon completing the "JWT Issue" value. You can configure your OIDC application using the information found at the URL. |
| Authorization Grant Flow | The grant flow drop down requires the selection of a Grant type. The grant type means how the client application acquires an access token which can be used to authenticate a request to an API endpoint. Note: the grant type that you select here, must align with the grant flow that you define in your application. For this example, select Authorization Code from the drop down. |
| Client Authentication Type | Describes how credentials are passed to the authorization server. You can select between Basic Authentication and Request Body. |
| Default Scopes | Scopes in OAuth 2.0 provide a way to limit the amount of access that is granted to an access token. You can select the scopes from the dropdown. Note that Scopes in OpenIAM are resources and you can manage through the Resource Manager interface. See more: oAuth scopes. |
| Skip scope approval | Set this to Off. |
| Token expiration | Access token expires after the specified minutes of being idle. You can set this value to 30 minutes. |
| Use refresh token | Refresh tokens carry the information necessary to get a new access token. Whenever an access token is required to access a specific resource, a client may use a refresh token to get a new access token issued by the authentication server. In most cases, this value should be set to Off. |
| Protect by 2FA | Set this value to Off unless you want to use 2FA during the authentication process. |
The example represents an Authentication provider value configuration to be used with the test SpringBoot application that was referenced earlier in this section.
Upon saving the configuration, the system will generate the clientid and clientsecret which will be used by the oAuth 2.0 Client.

How to grant access to an application
To be able to access the service provider through the IdP, we must grant access to the service provider by associating it to an entitlement object such as a group/role. While this topic is described in detail in the access control section, the section below provides a brief reference to entitle an application through a role.
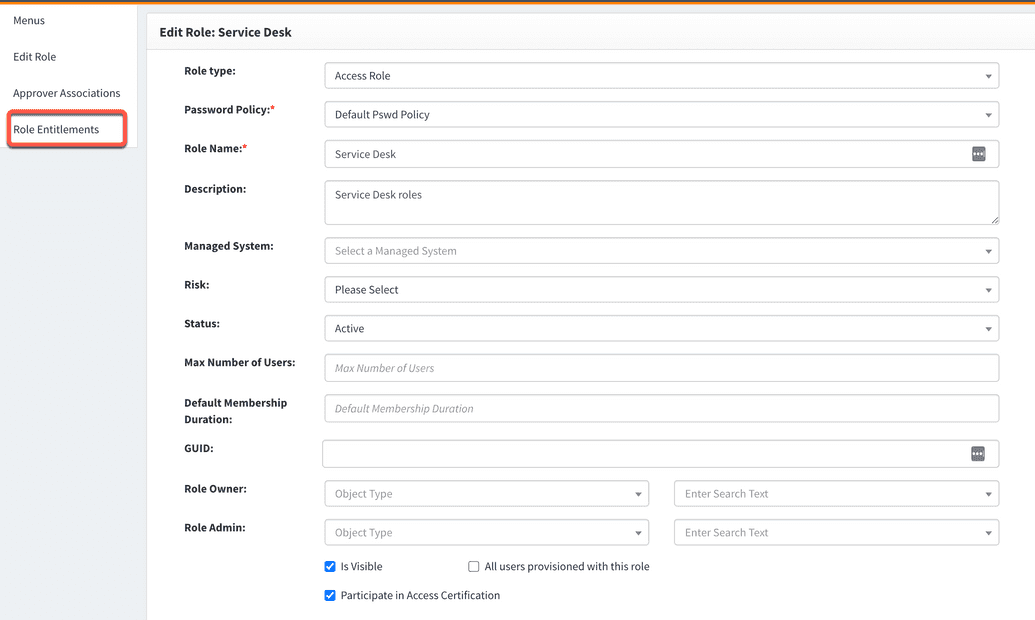
- Go to webconsole > Access Control > Role.
- Find an existing role which you want to update as entitled to your service provider.
- View the role details by clicking the icon in the Actions column.
- Go to the Role Entitlements option from the side menu as shown below.
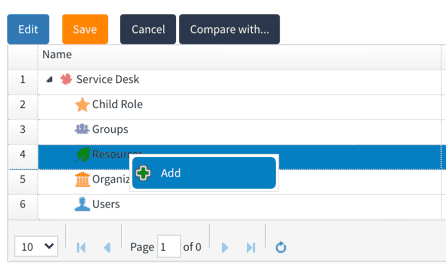
- Right click on Resource followed by select Add as shown below.
- From the Resource type drop down select Authentication provider.
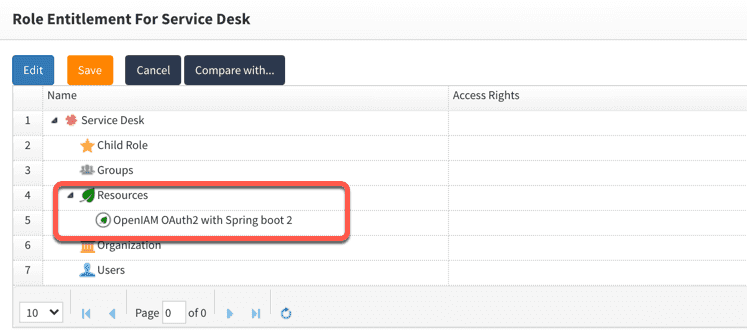
- From the adjacent dropdown, select the name of your authentication provider as shown below.
The role has now been entitled.
Note: Please, note that when using HMAC for signing JWTs in OAuth 2.0, we do not use public and private keys. HMAC relies on a shared secret key. Hence, if using HMAC signing algorithms (such as for Bynder.com, for example) will not contain any key.
In case you have set an authentication provider as IDP for OAuth protocol and the logs show the following message: JWT: The JWT returned by the token endpoint could not be validated against the retrieved JSON Web Key Set. Try using RSASSA-PKCS-v1_5 with SHA-512 signing algorithm and this will resolve the issue.