Configuring HTTPS on Docker
A first step in securing your deployment is to enable HTTPS in your docker installation. You will need to follow the process described below. The highlevel steps include:
- Generate a certificate from you CA. (You can use a use a self-signed if this is a non-production environment).
- Deploy the certificate
- Restart OpenIAM
- Validate that the https works
Generate a certificate
From your CA, please generate a certificate for your deployment. You will need the follow:
- Key file
- Certificate file
- SSL certificate chain file or SSL CA File
Update rProxy user access
The rProxy Docker container runs as user rproxy with uid = 75001 in the Docker container. Since the rproxy Docker container is not running as root, it has no access by default to the /opt/openiam/httpd directory. To configure access to it:
- The user 'rproxy' with uid = 75001 should be created on the host machine
- The directory: /opt/openiam/httpd directory should be configured to have read access for user 'rproxy'.
The rproxy Docker container can then map directories under /opt/openiam/httpd to Docker volumes and use certificates and keys stored there.
sudo groupadd -g 75001 rproxysudo useradd --shell /sbin/nologin -u 75001 -g 75001 rproxy
Create the folders to deploy the certificate on the OpenIAM host
By default, the certificates and keys are stored in the /opt/openiam/httpd/ssl-certs and the /opt/openiam/httpd/ssl-keys respectively. This location is defined in the openiam-docker-compose/3.2/rproxy-ssl/docker-compose.yaml file. Unless, you change this location, the certificates and keys must be in these two folders.
Create the required certificate folders using the steps described below:
sudo mkdir /opt/openiamsudo mkdir /opt/openiam/httpdsudo mkdir /opt/openiam/httpd/ssl-certssudo mkdir /opt/openiam/httpd/ssl-keyssudo chown -R rproxy /opt/openiam/httpdsudo chmod -R 755 /opt/openiam/httpd/ssl-certssudo chmod -R 700 /opt/openiam/httpd/ssl-keys
Deploy the certificate
Next copy the certificate files to the appropriate directories. If you are using the above defaults.
Update OpenIAM configuration
The use the certificates and to enable https, please update the following variables in the openiam-docker-compose/env.sh.
| Variable Name | Description |
|---|---|
| OPENIAM_RPROXY_HTTP | Set this to 0 enable HTTPS. Set it to 1 to disable https |
| OPENIAM_SSL_CERT | Name of the cert file; ie. mycert.crt Do not include the path |
| OPENIAM_SSL_CERT_KEY | Name of the key file; ie. mycert.key Do not inclue the path. |
| OPENIAM_SSL_CA | Name of the SSL CA certificate. This file should be in the same folder as the cert file. |
In a multi-node environment, copy these files to other Docker nodes in the same directories too. Or, configure the /opt/openiam/httpd directory so that it can be accessed from multiple nodes.
For these changes to take effect, you need to re-start OpenIAM. Use the ./shutdown.sh and ./start.sh utilities on the docker compose directory as you did during the installation process. Ensure that all services have stopped before re-starting.
Validating the configuration
There are several way to validate that your configuration for enabling SSL is working correctly. These are described below.
Inspect the rProxy container
Get the container ID of the rProxy by running the following
docker ps | grep rproxy
Use the container ID from the output to check the Apache webserver and rProx logs:
docker logs -f [container id]
Use the container ID in conjunction with the docker inspect to validate that our certificate directories have been mounted.
docker inspect [container id]
You will a section that looks similar to this:
"Mounts": [{"Type": "bind","Source": "/opt/openiam/httpd/ssl-certs","Destination": "/opt/openiam/httpd/ssl-certs","Mode": "","RW": true,"Propagation": "rprivate"},{"Type": "bind","Source": "/opt/openiam/httpd/ssl-keys","Destination": "/opt/openiam/httpd/ssl-keys","Mode": "","RW": true,"Propagation": "rprivate"}
Testing using Curl
You can test the https URL using curl as shown below
curl -k https://localhost/idp/actuator/health
If https is enabled, you will see a command similar to the one shown below.
{"status":"UP"}[root@iam-docs openiam-docker-compose]
From the browser
The final validation is the access the OpenIAM application from the UI using either one of the following application URLs:
https://[host name]/webconsolehttps://[host name]/selfservice
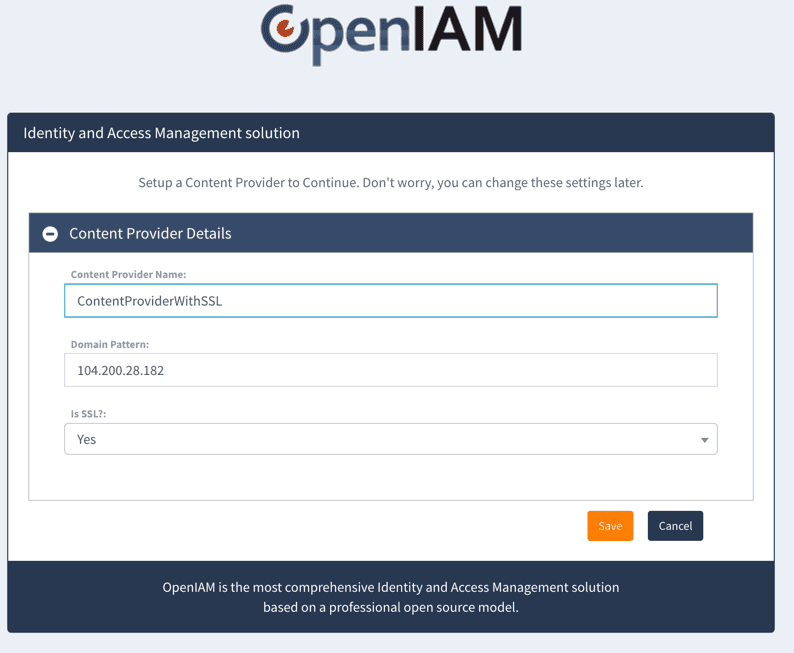
If this is this the first time that you are logging using SSL, then the system will ask you the set another content provider. Configure it as you did during the installation process, except ensure that the Is SSL? is set to Yes as shown in the image below.