Setting up Kerberos via rProxy
Host details of demo setup
| Host | IP (Demo Setup) | Description |
|---|---|---|
| rproxy.openiamtest.com | 10.1.0.6 | CentOS host where rProxy is configured. |
| DC1.openiamtest.com | 10.1.0.4 | Windows active directory to act as the KDC. |
| PC1.openiamtest.com | 10.1.0.5 | Client machine where the user will login and perform SSO. |
Configuring Active directory and creating a Keytab file
- Using an existing active directory and openiamtest.com domain configure rProxy host.
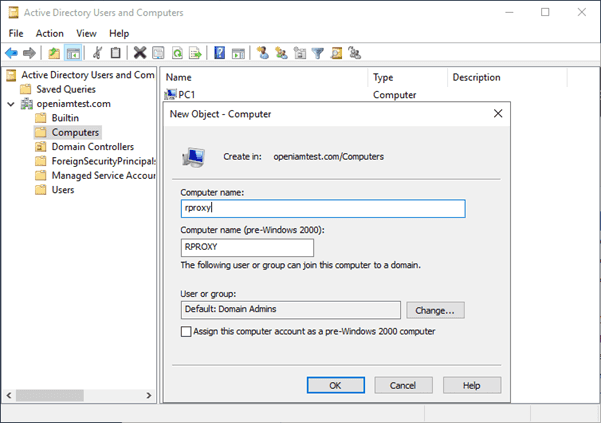
Go to Active Directory Users and Computers -> Right Click on Computers -> Click New. Then enter the details of the rProxy host as shown below and click OK.
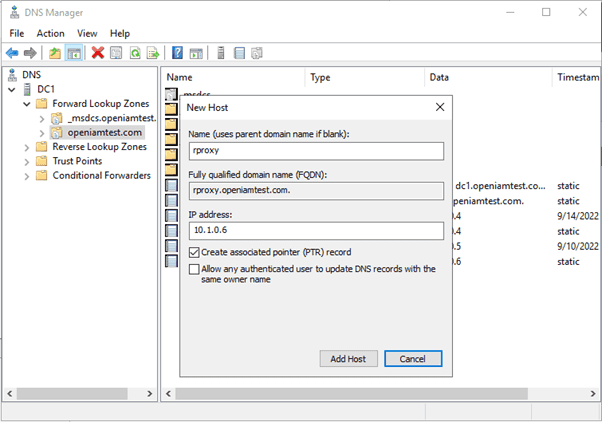
Next, open DNS Manager and expand Forward Lookup Zones folder and right click on openiamtest.com. Click on New Host (A or AAAA), enter details of rProxy host, check Create Associated Pointer (PTR) option and click Add Host.
- Create Service Principal and generate a keytab file.
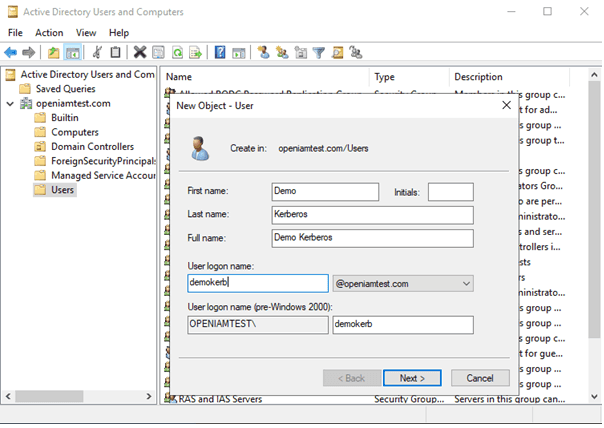
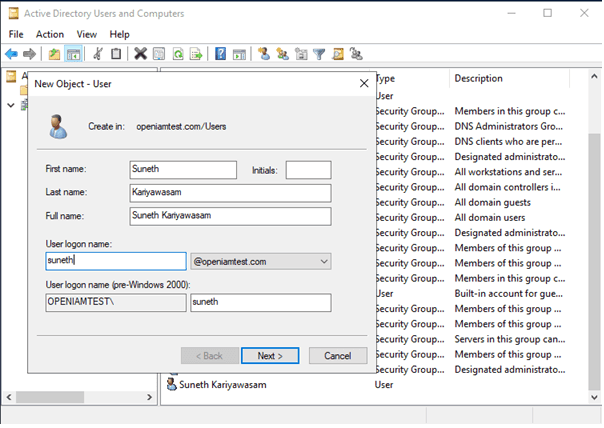
Go to Active Directory Users and Computers, click on Users and add two users as dummy Kerberose accounts for the rProxy hosts and an actual domain user to login to the client's Windows machine that performs SSO.
- Create Service Principal and Generate Keytab file.
Open a Command Prompt as Administrator and run below command to create the service principal. Use Domain Controller name as the last parameter.
setspn -U -S HTTP/rproxy.openiamtest.com DC1
Generate the keytab file using below command. Once the command is run the keytab file will be generated in d:\. Further, use the demokerb user’s password with -pass parameter
ktpass -princ HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM -mapuser demokerb@OPENIAMTEST.COM -crypto all -ptype KRB5_NT_PRINCIPAL -pass demokerb -out d:\krb5.keytab
Configuring rProxy host
- Set the hostname of rProxy as the root user.
hostnamectl set-hostname rproxy.openiamtest.com
- Edit /etc/hosts file to match below.
[root@rproxy ~]# cat /etc/hosts127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4::1 localhost localhost.localdomain localhost6 localhost6.localdomain610.1.0.6 rproxy.openiamtest.com ui esb10.1.0.4 dc1.openiamtest.com
Install rProxy using rpm or source. For reference, you may use rProxy setting up document.
Install dhcp-client with
Yum install dhcp-clientand edit /etc/dhcp/dhclient.conf as using commands below.
[root@rproxy conf.d]# cat /etc/dhcp/dhclient.confsend host-name "rproxy.openiamtest.com";supersede domain-name-servers 10.1.0.4;supersede domain-search "openiamtest.com";request subnet-mask, broadcast-address, time-offset, routers, domain-search, domain-name, domain-name-servers;require subnet-mask, domain-name-servers;timeout 300;retry 60;
- Verify process with nslookup.
[root@rproxy conf.d]# nslookup> dc1Server: 10.1.0.4Address: 10.1.0.4#53Name: dc1.openiamtest.comAddress: 10.1.0.4> pc1Server: 10.1.0.4Address: 10.1.0.4#53Name: pc1.openiamtest.comAddress: 10.1.0.5>
- Configure rProxy.
Navigate to /etc/httpd/conf.d/ and modify mod_openiam.conf or mod_openiam_ssl.conf based on the scheme shown below, find the <Location /> block.
<Location />AuthType openiamAuthName "OpenIAM"Require valid-openiam-federationRequire openiam-configureOPENIAM_DefaultUrl /selfservice/OPENIAM_Kerberos onOPENIAM_KrbPrincipalOnly onGssapiSSLonly OffGssapiCredStore client_keytab:/etc/krb5.keytabGssapiBasicAuth OffGssapiAllowedMech krb5GSSapiImpersonate offOPENIAM_CSPEnabled onOPENIAM_CORSAllowAll on#OPENIAM_SoapAuthHeaders "//*[local-name()='authentication'][1]"</Location>
Make sure to append the following
OPENIAM_Kerberos onOPENIAM_KrbPrincipalOnly onGssapiSSLonly OffGssapiCredStore client_keytab:/etc/krb5.keytabGssapiBasicAuth OffGssapiAllowedMech krb5GSSapiImpersonate off
- Install Kerberose software using below command.
yum install krb5-libs krb5-workstation
- Edit /etc/krb5.conf file using the content below.
[root@rproxy conf.d]# cat /etc/krb5.conf
Configuration snippets may be placed in this directory as well.
includedir /etc/krb5.conf.d/[logging]default = FILE:/var/log/krb5libs.logkdc = FILE:/var/log/krb5kdc.logadmin_server = FILE:/var/log/kadmind.log[libdefaults]#default_ccache_name = KEYRING:persistent:%{uid}default_realm = OPENIAMTEST.COMdefault_keytab_name = FILE:/etc/krb5.keytabdns_lookup_realm = falsedns_lookup_kdc = falseticket_lifetime = 24hrenew_lifetime = 7dforwardable = true[realms]OPENIAMTEST.COM = {kdc = dc1.openiamtest.comadmin_server = dc1.openiamtest.comdefault_domain = openiamtest.com}[domain_realm].openiamtest.com = OPENIAMTEST.COMopeniamtest.com = OPENIAMTEST.COM
- Copy the keytab file generated on Domain Controller to /etc/krb5.keytab and change permissions.
chown apache /etc/krb5.keytabchmod 0600 /etc/krb5.keytab
- Test if Kerberos works.
[root@rproxy conf.d]# kinit -V -k -t /etc/krb5.keytab HTTP/rproxy.openiamtest.comUsing default cache: /tmp/krb5cc_0Using principal: HTTP/rproxy.openiamtest.com@OPENIAMTEST.COMUsing keytab: /etc/krb5.keytabAuthenticated to Kerberos v5[root@rproxy conf.d]# klist -ke /etc/krb5.keytabKeytab name: FILE:/etc/krb5.keytabKVNO Principal---- --------------------------------------------------------------------------7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (des-cbc-crc)7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (des-cbc-md5)7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (arcfour-hmac)7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (aes256-cts-hmac-sha1-96)7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (aes128-cts-hmac-sha1-96)[root@rproxy conf.d]# kvno HTTP/rproxy.openiamtest.comHTTP/rproxy.openiamtest.com@OPENIAMTEST.COM: kvno = 7[root@rproxy conf.d]# klist -eTicket cache: FILE:/tmp/krb5cc_0Default principal: HTTP/rproxy.openiamtest.com@OPENIAMTEST.COMValid starting Expires Service principal09/14/2022 07:02:48 09/14/2022 17:02:48 krbtgt/OPENIAMTEST.COM@OPENIAMTEST.COMrenew until 09/21/2022 07:02:48, Etype (skey, tkt): aes256-cts-hmac-sha1-96, aes256-cts-hmac-sha1-9609/14/2022 07:04:17 09/14/2022 17:02:48 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COMrenew until 09/21/2022 07:02:48, Etype (skey, tkt): arcfour-hmac, arcfour-hmac
NOTE: Ticket's kvno must match kvno in keytab. The principal name in ticket must match the principal name in keytab. The enctype in ticket and keytab must also match. Verify the following command output.
7 HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM (arcfour-hmac)
HTTP/rproxy.openiamtest.com@OPENIAMTEST.COM: kvno = 7
HTTP/rproxy.openiamtest.com@OPENIAMTEST.COMrenew until 09/21/2022 07:02:48, Etype (skey, tkt): arcfour-hmac, arcfour-hmac
- Restart httpd service.
Configuring OpenIAM
- Login to OpenIAM and create a content provider to match the domain pattern and add “Def. Kerb Auth Rule” under Supported Authentication Rules.
- Edit URL patterns /idp/oauth2/authorize, /idp/oauth2/handler and add “Def. Kerb Auth Rule” under Supported Authentication Rules.
- Create a user with the same username as domain user (or use a supported connector to authenticate the principal with domain controller).
Configuring Client Machine
- Add client PC1 to the domain controller.
- Edit Internet Options.
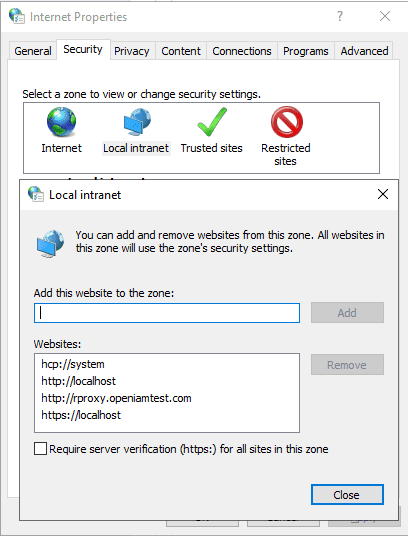
Go to internet options and click on security then local intranet then add http://rproxy.openiamtest.com
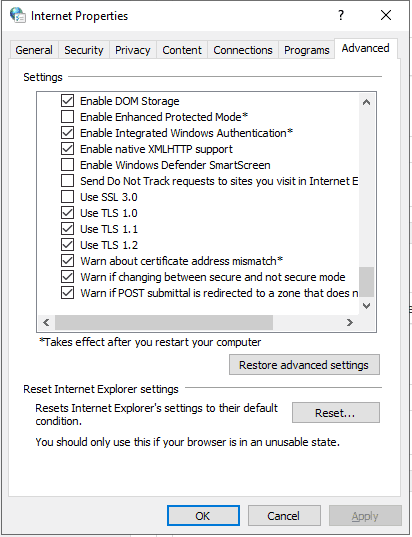
Then click on Advance and check “Enable Integrated Windows Authentication*”.
Restart client machine if required.
- On the client machine, open a browser (IE, Chrome), navigate to http://rproxy.openiamtest.com/selfservice/ and verify the SSO.