Access Rights
Access right in OpenIAM is a tag for user-role, user-group, user-resourse etc. relationships. OpenIAM uses acess right as a tag only, not limiting the user by the presence/absene of an access right.
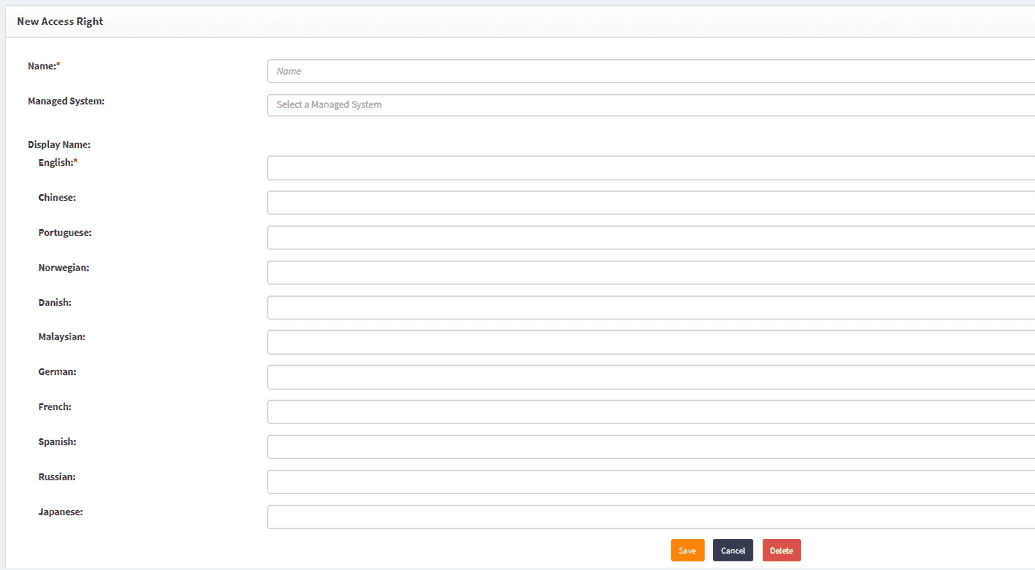
User can create new access rights and link them to Managed system as needed. To do that, go to Access control tab -> Access Rights -> New Access Right in the left-hand menu.
Since access rights are visible in SelfService, there are options for localization of its name.
Pick the name for a new access right and select a managed system to link it with and click Save.
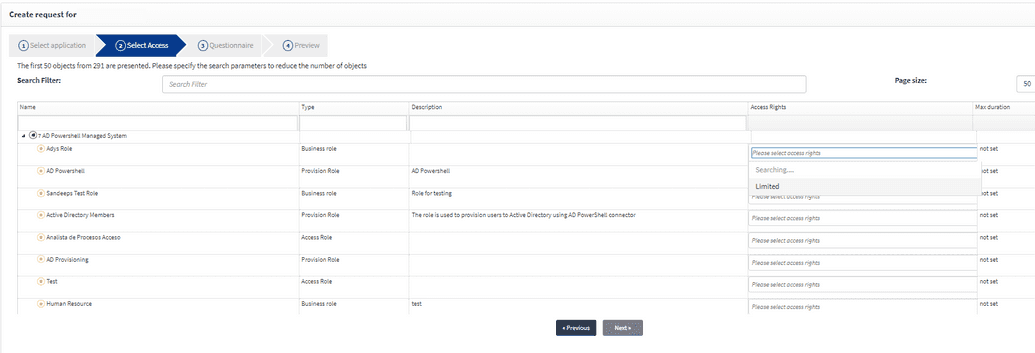
In case an access right is linked to any Managed system, user can see it when creating a request. To see it go to selfservice -> Create request -> Select from servicce catalogue -> Directories -> choose your Managed System and in the Access Rights column dropdowns there will be the access right you've created.
Those access rights that are not linked to Managed System will not be displayed here.
There are three default access rights that need to be discussed deeper - 'Admin Access', 'IsCertified' and 'Owner Access'.
User needs to add 'IsCertified' access right to those relationships between role or group, participating in Access Certification.
'Admin Access' and 'Owner Access' in their turn are visible in the admin or owner attributes for role, group or resource. In case when editing role/group/resource, one will set themself as Role Owner and Role Admin, they become a member of this role/group/resource. It means that a user is owner and admin for this role in OpenIAM only and it doesn't mean that the user becomes an admin or an owner in the target system, unless it was defined in Policy Map for provisioning.
Hence, if the target system supports such type of an entitlement (owner, admin) tag and while provisioning the user pushed Access Right in the policy map then having these tags in OpenIAM also means having same access right in the target system. It is important to remember that access rights duplication is not performed automatically.