Help desk profile protection
Overview
OpenIAM provides controls to safeguard user profiles from fraudulent access during help desk support sessions. When the end user calls for support, the help desk technician will pull up the user’s profile which will prompt the technician to ask the user questions unique to their profile to verify their identity in order for the technician to gain access to the end user’s profile. Upon successful verification, the user profile will be unlocked to the help desk technician who can then proceed to provide assistance to the end user.
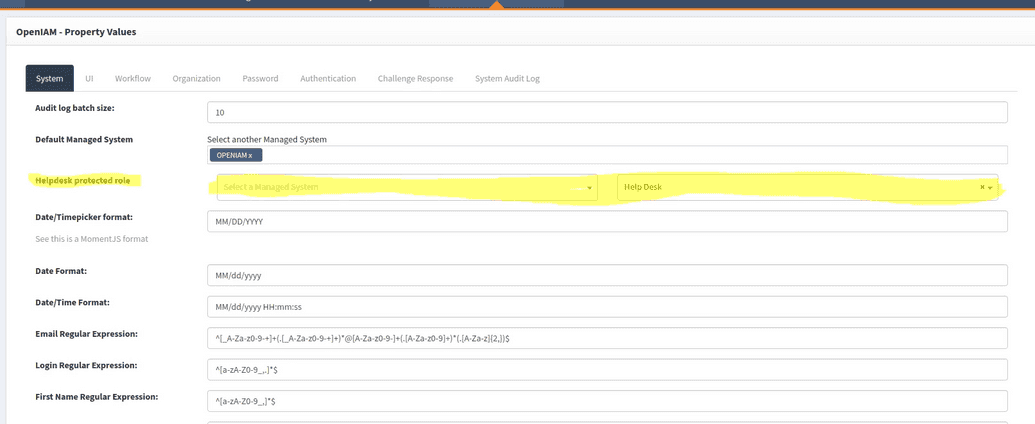
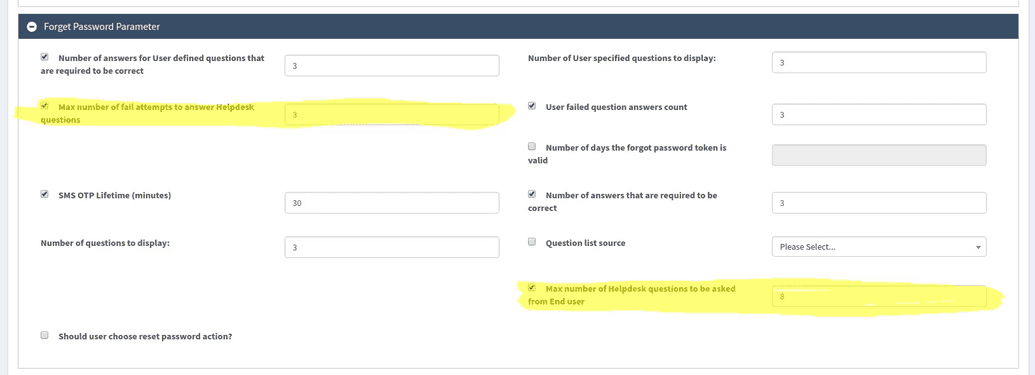
Help desk profile protection is enabled when the Help desk protected role is assigned to the role of appropriate help desk personnel (described below). When it is not assigned, the help desk profile protection workflow is disabled. If the end user fails to answer questions correctly after x number of attempts, the profile will be blocked to the help desk. (Note: the number of allowed failed attempts as well as the number of questions to be asked by help desk technicians is configurable from within the webconsole). Unblocking of the profile will be executed by a batch script based on a cron job.
Help desk questions
The set of questions required for help desk personnel to gain access to a user’s profile are compiled from contact information and user fields. By default, the workflow is set to use:
- Title
- Middle initial
- Employee ID
- Birthday
- User secret - encrypted with user key
The system will generate questions from objects that do not contain a null value.
Example
In this example, the system is configured to require help desk personnel to ask end users three questions to gain access to their profile. An end user named John Silver has the following profile information:
| First Name | Last Name | Title | Employee ID | Birthday | Initials | Email Address |
|---|---|---|---|---|---|---|
| John | Silver | Developer | 11/11/1986 | P | john.silver@company.org |
John Silver calls the help desk and provides the technician with his first name, last name and phone number.
The information provided by John Silver is sufficient for the technician to locate his profile through the search parameters.
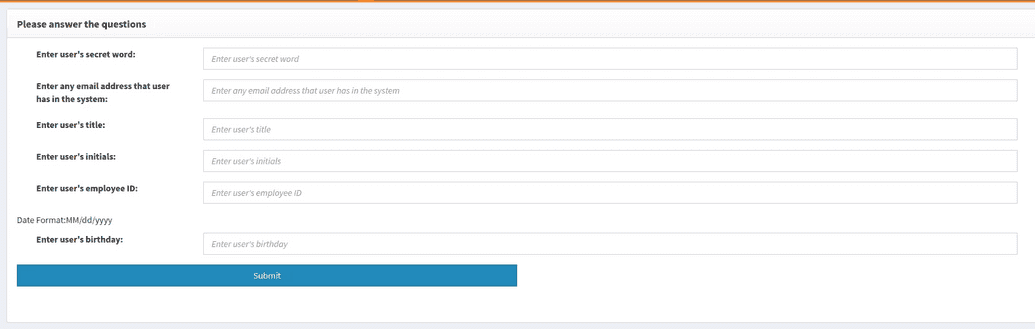
To unlock his profile to the help desk technician, John Silver is asked for his job title, birthday and user secret.
Upon successful verification, the profile is unblocked to the technician who can then proceed to provide support to John Silver.
User secret
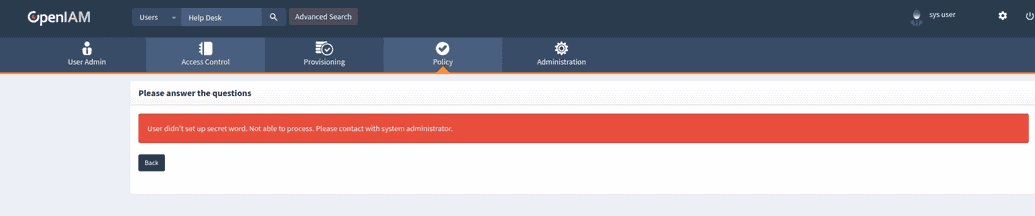
End users will always be required to provide their user secret to help desk personnel in order to unlock their profile to the technician. If the user secret was not set, then the help desk technician will be unable to unlock the end user's profile.
The end user is prompted to set a user secret during first time login if the property org.openiam.am.helpdesk.role.ids is set. While OpenIAM does not allow the user to change their user secret, the user secret can be reset via the reset account functionality.
Configuration
Select Administration > System Configuration and select the System tab. Assign Helpdesk protected role to the role attributed to help desk personnel. If this is not assigned, the help desk profile protection workflow is disabled.
Select Policy > Password Policy, and select the Policy Name. Under the section labeled Forgot Password Parameter, set values for the maximum number of allowed failed attempts to answer help desk questions and the maximum number of help desk questions to be asked to the end user as shown in the screenshot below.
An example of the help desk profile protection page is shown in the screenshot below.
If the end user did not create a user secret, the help desk technician will be notified when the profile is located.
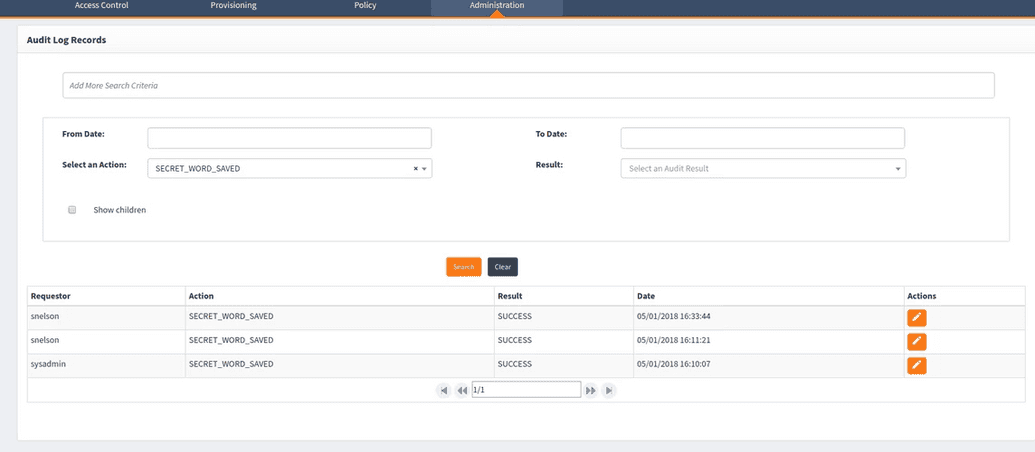
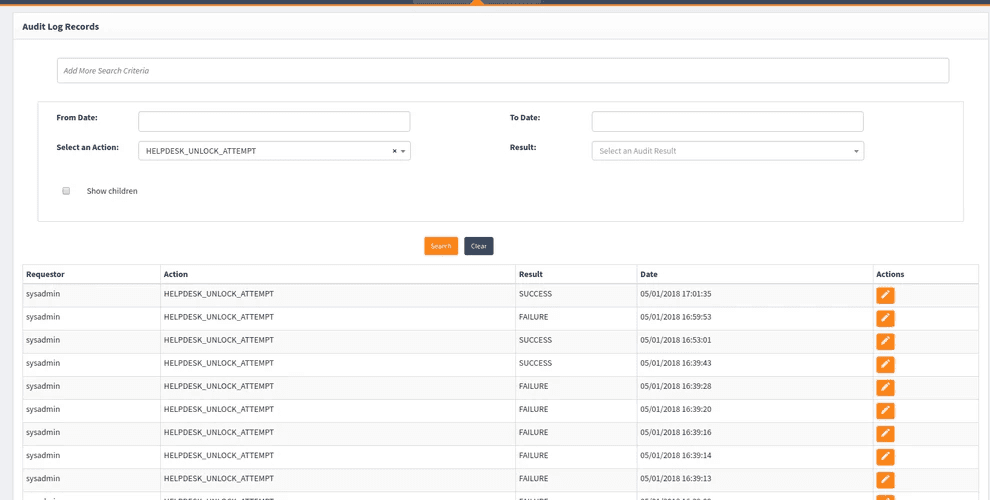
Audit logging
Select Administration > Log Viewer.
- To view a log of users who have saved their user secret, select Select an Action > SECRET_WORD_SAVED and select Search. (AuditAction = SECRET_WORD_SAVED)
- To view a log of attempts by help desk technicians to unlock user profiles, select Select an Action > HELPDESK_UNLOCK_ATTEMPT and select Search. (AuditAction = HELPDESK_UNLOCK_ATTEMPT)