FIDO-2 Authentication
This section describes how to configure authentication using FIDO 2.
Note: FIDO 2 is only supported in version 4.2.1 and later.
Note: FIDO-2 can only be used over HTTPS
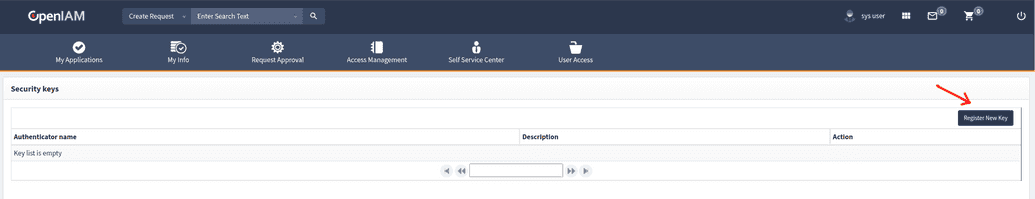
1. Manage authenticators
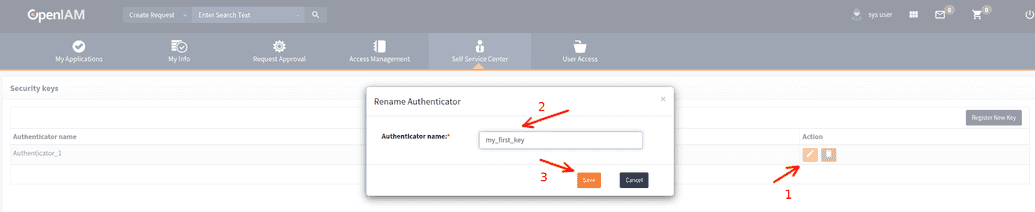
Add new authenticator, rename it or delete - use OpenIAM UI manager on self-service :
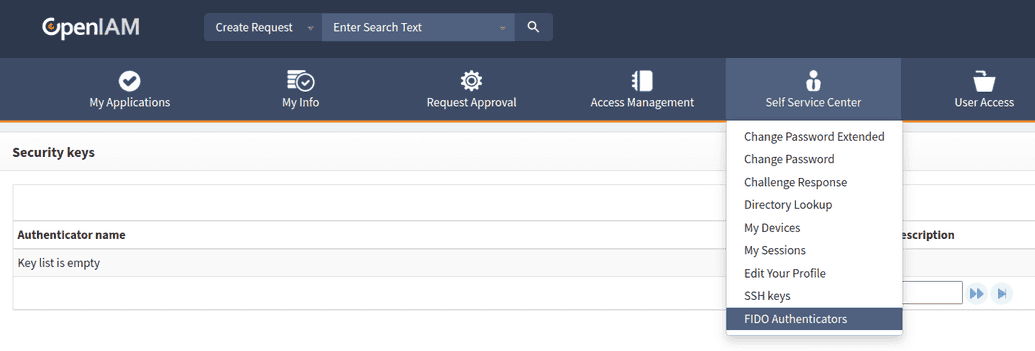
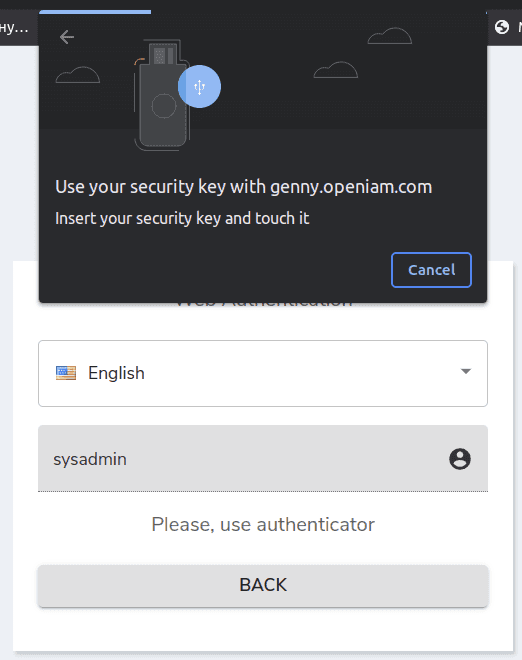
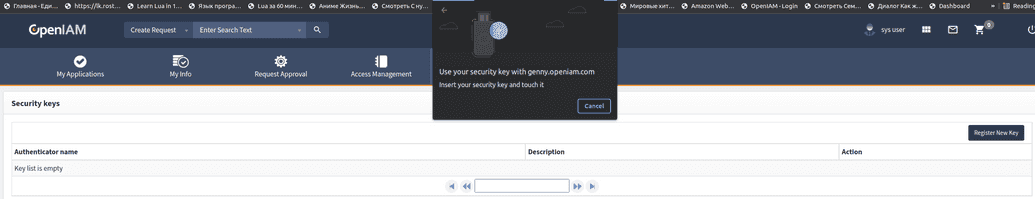
Touch ssh key after browser message appear
2. Configure OpenIAM to use FIDO authentication
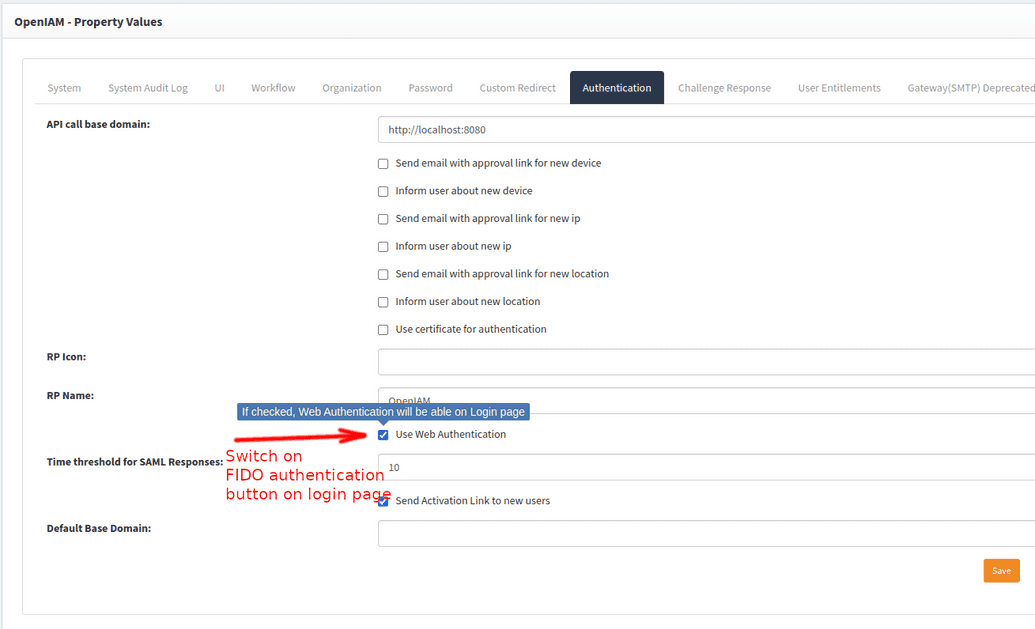
1. Check "Use Web authentication" flag on "System configuration page"
2. Use default authentication rule in content provider:
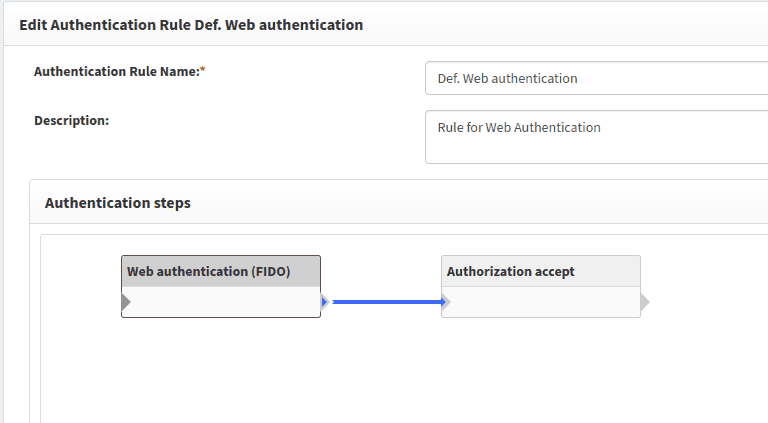
or create new custom authentication rule. For example:
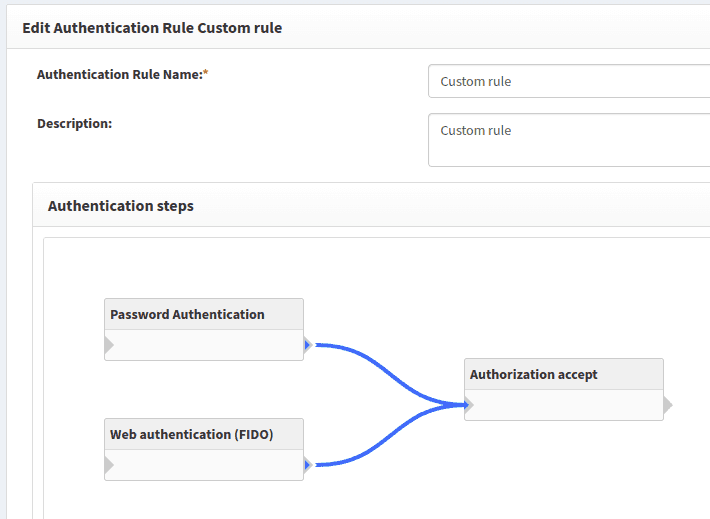
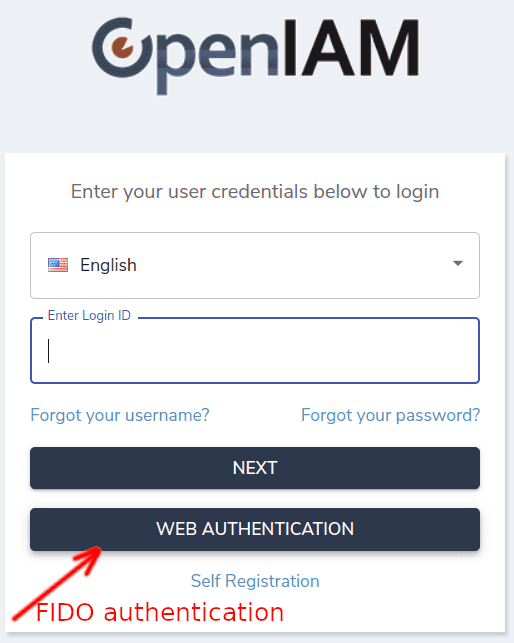
3. Login with FIDO authenticator
4. Some API for FIDO-2 authentication
Preregistration request.
/idp/reg/preregister POSTrequest :{username : login,displayName : displayName}response :{rp: data.rp,user: {id: decodeBase64url(data..id),name: data..name,displayName: data..displayName,icon: data..icon},challenge: decodeBase64url(data.challenge),pubKeyCredParams: data.pubKeyCredParams,timeout: data.timeout,excludeCredentials: data.excludeCredentials,// {// type: credential.type,// id: decodeBase64url(credential.id),// transports: credential.transports// }authenticatorSelection: data.authenticatorSelection,attestation: data.attestation,extensions: data.extensions}
Registration request.
/idp/reg/register POSTrequest:{name : authenticatorName,id = credential.id;type = credential.type;rawId = encodeBase64url(new Uint8Array(publicKeyCredential.rawId));clientData = encodeBase64url(new Uint8Array(clientData));attestationObject = encodeBase64url(new Uint8Array(attestationObject));clientExtensionsJSON = clientExtensionsJSON;}response:{successMessage : "Authenticator saved"}
Pre-authentication request.
/idp/auth/preauthenticate POSTrequest:{username : authenticatorName,userVerification = credential.id;extensions = credential.type;}response:{challenge: decodeBase64url(data.challenge),timeout: data.timeout,rpId: data.rpId,allowCredentials: data.allowCredentials// {// type: credential.type,// id: base64url.decodeBase64url(credential.id),// transports: credential.transports// }userVerification: data.userVerification,extensions: data.extensions}
Authentication request.
/idp/auth/authenticate POSTrequest:{credentialId = encodeBase64url(new Uint8Array(publicKeyCredential.rawId));clientDataJSON = encodeBase64url(new Uint8Array(clientDataJSON));authenticatorData = encodeBase64url(new Uint8Array(authenticatorData));signature = encodeBase64url(new Uint8Array(signature));clientExtensionsJSON = JSON.stringify(clientExtensions);}