LDAP connector
The LDAP connector can be used with any directory which supports the LDAP and LDAPS protocols such as OpenLDAP, Active Directory or eDirectory.
Installing the connector
The steps below describe how to install and start the connector. Depending on whether you are using Kubernetes, Swarm or RPM, the instructions will vary.
RPM File
First, download jar file into /usr/local/openiam/connectors/bin and change owner to OpenIAM user.
wget https://download.openiam.com/release/enterprise/4.2.1.4/connectors/ldap-connector-rabbitmq.jarchown openiam:openiam /usr/local/openiam/connectors/bin/ldap-connector-rabbitmq.jar
Next, create a new .sh file for starting LDAP connector by running:
nano ldap_start.sh
Content of the file:
#!/bin/bash. /usr/local/openiam/env.confexport VAULT_CERTS="$HOME_DIR/vault/certs/"export JAVA_HOME="$HOME_DIR/jdk"export JAR_FILE="ldap-connector-rabbitmq"export JAVA_OPTS="-Xmx256m -Djdk.tls.client.protocols=TLSv1.2"su openiam -c "$JAVA_HOME/bin/java -Dlogging.level.root=ERROR -Dlogging.level.org.openiam=ERROR -Dconfpath=$HOME_DIR/ -Djavax.net.ssl.keyStorePassword=changeit -Djavax.net.ssl.trustStore=$HOME_DIR/conf/$JAR_FILE/ -jar $JAVA_OPTS $HOME_DIR/connectors/bin/$JAR_FILE.jar > $HOME_DIR/logs/$JAR_FILE.log&"
Make file executable by running:
chmod +x ldap_start.sh
To start the connector, use the following command:
./ldap_start.sh
Docker Swarm
Kubernetes
Synchronization
OpenIAM provides two pre-configured synchronization options for the LDAP connector:
- OpenLDAP User
- Matches users by
User ID.
- Matches users by
- OpenLDAP Group
- Matches groups by
nameandcn.
- Matches groups by
To access synchronization settings:
- Log in to the Web Console.
- Navigate to Provisioning > Synchronization.
- Search for
OpenLDAP UserorOpenLDAP Group.
Both synchronization configurations come with example transformation scripts.
Enabling attributes in LDAP connector
To enable attributes in the LDAP connector, start by logging in to the OpenIAM Web Console.
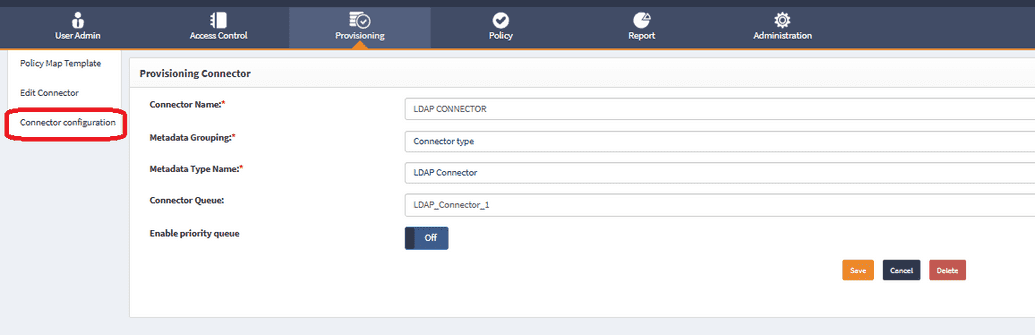
- Navigate to Provisioning > Connectors.
- Find the LDAP connector and click Edit.
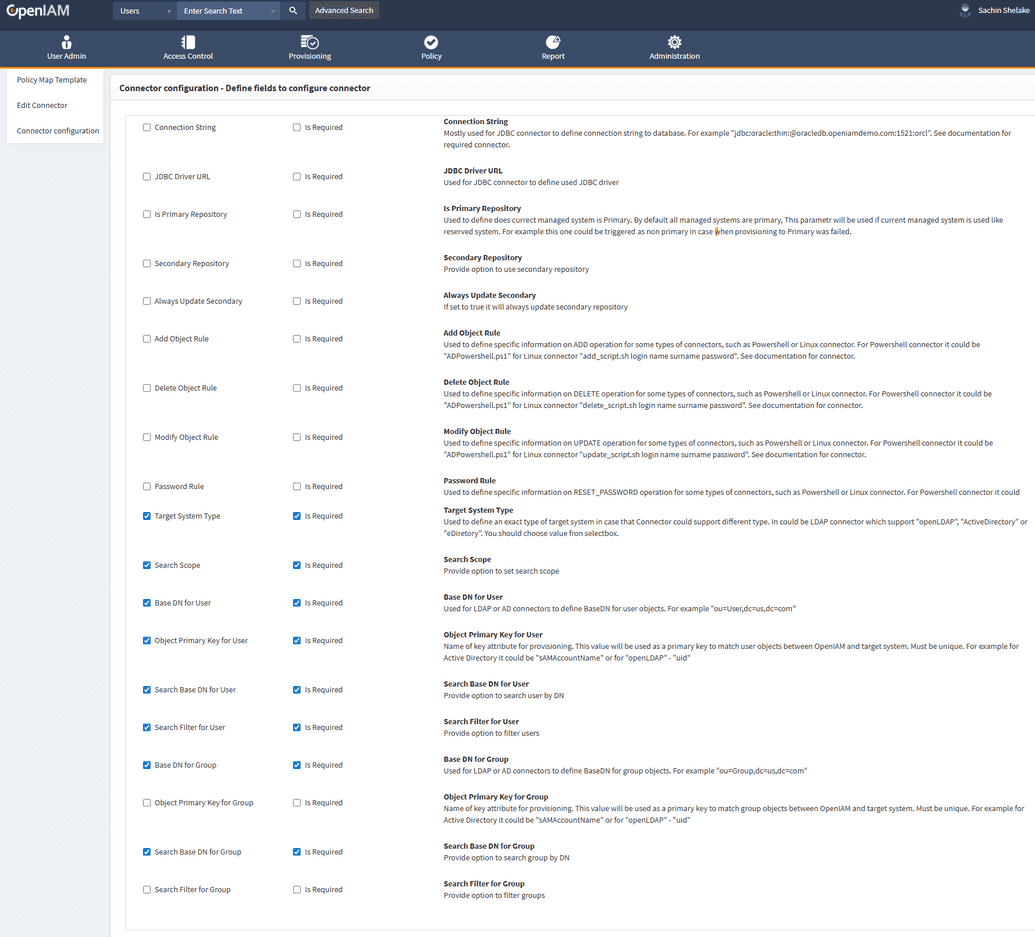
- In the left-hand menu, find the Connector Configuration option and click it.
- In the window that opens, select the checkbox(es) based on your requirements. In the example below, the Base DN for Group and Search Base DN for Group checkboxes are enabled.
- Click Save. Proceed with configuring the Managed System.
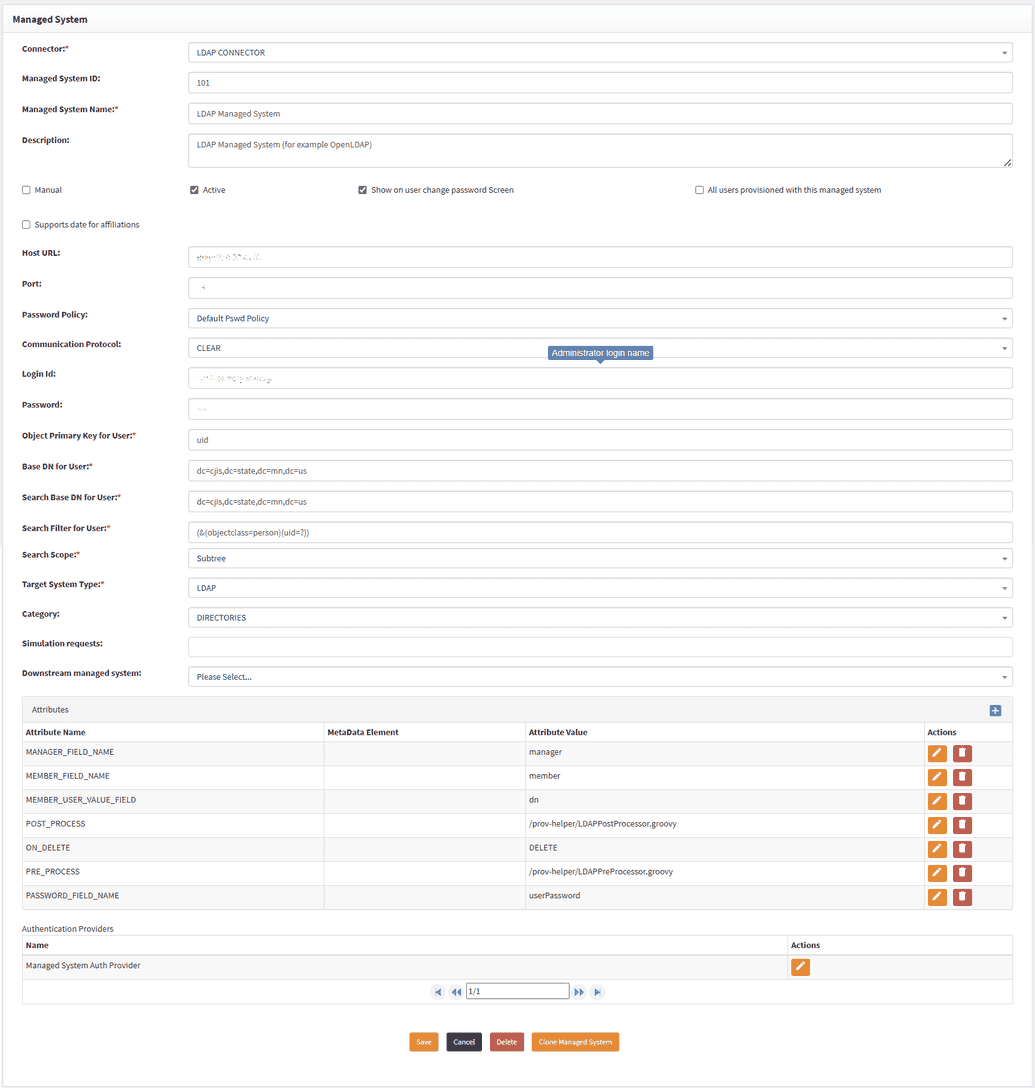
Configuring managed system
OpenIAM has a built-in Managed System configuration named OpenLDAP, which can be found by logging in to the Web Console and going to Provisioning > Managed System. It can be used as is, as it is already pre-configured. If you choose to configure the managed system from scratch, you must fill in the fields manually.
To configure attributes for a Managed System, follow the steps below:
- Provide all required details and verify that Base DN and Search Base DN are present for both Group and User. If not, add them.
Example:
- Base DN for Group:
ou=groups,dc=ldap,dc=local - Search Base DN for Group:
ou=groups,dc=ldap,dc=local
Configure Synchronization for OpenLDAP User and OpenLDAP Group as described above. Verify each configuration in both OpenLDAP User and OpenLDAP Group, and update the necessary details as needed.
The transformation rule to be used is
LdapGroupTransformationScript.groovy. This script can be found using the search engine under Administration > Groovy Manager, or see the full script below.
package org.openiam.sync.service.implimport org.apache.commons.collections4.CollectionUtilsimport org.openiam.base.AttributeOperationEnumimport org.openiam.idm.srvc.grp.dto.Groupimport org.openiam.idm.srvc.grp.dto.GroupAttributeimport org.openiam.idm.srvc.meta.domain.MetadataTypeGroupingimport org.openiam.idm.srvc.synch.dto.LineObjectimport org.openiam.idm.srvc.user.dto.Userimport org.openiam.provision.dto.ProvisionUserimport org.openiam.sync.service.impl.service.AbstractGroupTransformScriptclass LdapGroupTransformationScript extends AbstractGroupTransformScript {@Overrideint execute(LineObject rowObj, Group group) {println "** - Group Transformation script called."try {group.setPolicyId("4000");def ldapMdType = getMetadataTypeByNameAndGrouping("LDAP group", MetadataTypeGrouping.GROUP_TYPE);if (ldapMdType)group.setMdTypeId(ldapMdType.getId())elsegroup.setMdTypeId("GENERAL_GROUP")populateObject(rowObj, group)} catch (Exception ex) {ex.printStackTrace();println "** - Transformation script error."return -1;}println "** - Transformation script completed." + groupreturn NO_DELETE}private void populateObject(LineObject rowObj, Group group) {def columnMap = rowObj.columnMapgroup.name = columnMap.get("cn")?.valuegroup.managedSysId = config.getManagedSysId()group.description = columnMap.get("displayName")?.valueif (group.getDescription() && group.getDescription().length() > 254) {group.setDescription(group.getDescription().substring(0, 254));}group.status = "ACTIVE"addGroupAttribute(group, "gidNumber", columnMap.get("gidNumber")?.value);addGroupAttribute(group, "dn", columnMap.get("dn")?.value);def obj = columnMap.get("objectClass")if (obj.valueList.contains("posixGroup")) {println "Objectclass ${obj.valueList}"def membersAttr = columnMap.get("memberUid")if (membersAttr) {def members = membersAttr.valueListif (members) {addGroupMembers(group, members)}}} else if (obj.valueList.contains("groupOfNames")) {println "Objectclass ${obj.valueList}"def membersAttrs = columnMap.get("member")if (membersAttrs) {def members = membersAttrs.valueListif (members) {def uids = extractUids(members)if (uids) {addGroupMembers(group, uids)}}}}}List<String> extractUids(List<String> valueList) {return valueList.collect { entry ->def afterUid = entry.split("uid=")[1]def uid = afterUid.split(",", 2)[0]return uid}}private void addGroupMembers(Group g, List<String> users) {if (!isNewUser && CollectionUtils.isNotEmpty(users)) {for (String us : users) {User u = getUserByLogin(us, config.getManagedSysId())println "found member:" + u?.displayNameif (u != null) {if (g.getUser(u.getId()) == null) {try {Set<String> rights = new HashSet<>()rights.add("IS_CERTIFIED")u.addGroup(g, rights, null, null)userManager.save(new ProvisionUser(u), null)} catch (Exception e) {log.warn("Can't attach user to group.")}}}}}}@Overridevoid init() {}}
Review the LDAP schema and update the code as needed. For example, if the
objectClassisposixGroup, the member information is returned in thememberUidattribute; otherwise, it is in thememberattribute.Specify the attribute names to retrieve from LDAP (such as
member) in theSourceAttributesNamesGroovy script.
Connector troubleshooting tips
SSL connection issue
Symptoms:
org.openiam.connector.core.base.exception.ConnectorException: javax.naming.CommunicationException: simple bind failed: xxxxx.xx.xxx.xxx.xxx:636 [Root exception is javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target] Caused by: javax.naming.CommunicationException: simple bind failed: myldap.example.com:636
Solution:
Make sure port is open and reachable, and you can connect via telnet command
telnet myldap.example.com 636
If you are connecting to LDAP via secured port 636 you should import ca_cert issued by domain into java keystore:
keytool -noprompt -import -v -trustcacerts -alias ldap_ca$(pwgen -s 13 1) -file /path/to/ca_cert.crt -keystore /usr/local/openiam/jdk/lib/security/cacerts -keypass changeit -storepass changeit