Deploying via Docker
This section describes how to deploy the OpenIAM platform in a Docker Swarm environment. The procedures described in this section must be performed in the order that they are presented. Some steps in this installation require root level privileges to the system where OpenIAM will be deployed.
What is Docker?
Docker is a tool for creating, deploying, and running applications using containers. Docker Compose is a tool for defining and running multi-container Docker applications. Docker provides a standardized, lightweight, execution environment that maintains all dependencies within it. It can be run on either physical or virtualized environments which are on-premise or in the cloud. For more information about docker, please see see the Docker website and Docker Documentation.
OpenIAM on Docker
The OpenIAM Docker deployment method enables you to deploy on OpenIAM using a series of pre-configured containers in a short amount of time without the complexity of deploying a series of dependencies. The simplified deployment method requires:
- Installing the Docker software
- Configuring environment variables
- Running scripts for setting up and starting up the OpenIAM instance. Running the deployment scripts automatically takes care of all component dependencies and release updates.
OpenIAM docker containers are maintained on Docker hub. Once these containers have been pulled into your environment using the details below, you will also need:
- Docker client - Docker Community Edition (CE) versions 19.03.12 or higher
- Docker compose - Defines and enables the operation of a multi-container Docker application. OpenIAM uses
docker-composefile format 3.2
OpenIAM Solution Stacks
The OpenIAM solution consists of several stacks that are deployable the Docker Swarm. Docker swarm is a container orchestration tool, meaning that it allows for the manage multiple containers deployed across multiple host machines. The content of each stack is described below
Critical Infrastructure stacks
The infrastructure stacks are used across the OpenIAM solution regardless of the functionality that you are enabling. These components must be operational for the OpenIAM solution to function correctly.
| Stack Name | Description |
|---|---|
| Elasticsearch | Runs Elasticsearch. Elasticsearch is an enterprise-level search engine. Elasticsearch uses an index-based search approach, which allows for fast searching. The architecture allows for scalability, flexibility, and multi-tenancy support |
| Redis | Runs Redis. Redis is an in-memory data structure store used as a database, cache, and message broker by OpenIAM |
| MariaDB / PostgresSQL | Runs either MariaDB or PostgreSQL as the product repository. MariaDB is configured as the default repository. Aside from these two databases, you can also use a remote database |
| RabbitMQ | Runs RabbitMQ. RabbitMQ is the message brokering software service for sending and receiving messages between systems |
| Vault | Runs Hashicorp's Vault. Vault secures, stores, and tightly controls access to tokens, passwords, certificates, API keys, and other secrets |
| Etcd | Runs Etcd, which is used to store Vault data. Etcd is a distributed key-value store. |
MariaDB is the default Database. You can change this to PostgreSQL if you prefer. You will not enable both database
Service stacks
| Stack Name | Description |
|---|---|
| OpenIAM core services | Runs services shared across the product. |
| Identity manager | Runs the identity manager application. Identity manager automates the task of managing identities across various devices and applications used by the enterprise. |
| Workflow | Runs the workflow application. A workflow is a repeatable process during which documents, information, or requests are passed from one participant to another for action, according to a set of procedural rules. A participant can be a person, machine, or both. |
| Groovy manager | Runs Groovy Manager, an application for managing Groovy scripts in OpenIAM. Apache Groovy is a dynamic programming language for the Java platform. allows you to add, update, edit, and modify Groovy scripts to extend the identity governance and web access management functionality to meet specific, complex requirements. |
| Synchronization | Runs the synchronization application. Synchronization allows you to synchronize data from one or more authoritative sources to a set of managed systems. Synchronization configuration enables monitoring a source system for changes and then updating target systems at scheduled periodic intervals. |
| Reconciliation | Runs the reconciliation application. This is two side synchronization between OpenIAM and the target system |
| Authorization manager | Runs the authorization manager. This module handles RBAC authorization via relationships between Users, Organizations, Roles, Groups, and Resources. |
| E-mail Manager | Runs the email manager. Handles sending and receiving email. |
UI Stack
| Stack Name | Description |
|---|---|
| Tomcat with three applications | Three web applications which are described below |
- IdP - The OpenIAm web application which provides centralized authentication and self-service password reset functionality. This application also allows OpenIAM to be configured as both an Identity Provider and a Service Provider
- Webconsole - The OpenIAM web application for administrators for managing identities across various devices and applications used by an enterprise, and for controlling access to these devices and applications.
- Self-service - The OpenIAM end-user web application that allows users to create new requests, reset and change passwords, manage their profiles, manage access requests, manage challenge response security questions, look up corporate users through a directory search, and reset their accounts if they are locked out. Authorized users can also use the request approval functionality.
Reverse Proxy Stack
| Stack Name | Description |
|---|---|
| Apache Web server with rProxy | Gateway between clients and a server for managing inbound traffic to a server. |
System requirements
The table below specifies the minimum system requirements for deploying a non-production OpenIAM v4.2.x instance using Docker.
MINIMUM Hardware requirements
| Configuration | Non-Production | Production (may increase based on sizing) |
|---|---|---|
| Memory | 48 GB | 64 GB |
| CPU | 8 CPUs | 12 CPUs |
| Disk | 80 GB | 200 GB |
Please ensure that you are environment is aligned with the minimum system requirements described above. These parameters are not optional. OpenIAM will not start if system resources are below the minimum levels.
For production use: Customers with active subscriptions and partners, should contact OpenIAM Support (techsupport@openiam.com) for assistance with sizing requirements.
Software requirements
| Specification | Requirement |
|---|---|
| OS | Ubuntu (22.04 LTS, 20.04 LTS) or CentOS 8 Stream/RHEL 8.7+ |
| Docker client | 23.0.1 or higher |
| Docker compose | 1.28.2 or higher |
| Supported Browsers | Google Chrome (v89.0.4389.114 and later), Microsoft Edge, Mozilla Firefox (v87 and later). Note: Internet Explorer (IE) is not supported. |
Preparing your system
The OpenIAM application requires the configurations described below to be performed prior to installing the application.
Install pre-requisite packages
Prior to installing the OpenIAM, please execute the commands below to install the required packages. If you have already logged in as root, you do not need to prefix them with “sudo”. If you have used another account, then you need to use “sudo”
| Description | Command on CentOS 8 Stream | Command on Ubuntu |
|---|---|---|
| Update the OS | dnf update | apt-get update |
| Install Nano | dnf install nano | apt-get install nano |
| Install wget | dnf install wget | apt-get install wget |
| Install git | dnf install git | apt-get install git |
Example for CentOS 8 Stream
dnf updatednf install nano wget git
Example for Ubuntu 22.04
apt-get updateapt-get upgradeapt-get install nano wget git
Update the hosts file
Make sure that your /etc/hosts file contains a value for the hostname that you defined earlier. To edit the hosts file, use an editor like Nano.
127.0.0.1 iam-nonprod
Settings for ElasticSearch and Docker
ElasticSearch
OpenIAM uses ElasticSearch as a search engine. To enable fast access, ElasticSearch maps portions of an index into its memory address space. This is done through nmap, a Unix system call that maps files or devices into memory. To use mmap effectively, ElasticSearch requires sufficient mmap counts. The default operating system limits on mmap counts are inadequate for the required performance and this may result in out of memory exceptions. The required mmap value can be configured by setting the vm.max_map_count value in /etc/sysctl.conf to be at least 262144. To ensure that the vm.max_map_count persists across restarts, set this value in the /etc/sysctl.conf file
Disabling IPv6 on Docker Host
By default, IPv6 is disabled in Docker. Disabling IPv6 on Docker host(s) prevents any potential network issues. To disable IPv6 on host(s) where Docker is running, ensure that the Docker host(s) have the following value set in /etc/sysctl.conf: net.ipv6.conf.all.disable_ipv6=1 and net.ipv6.conf.default.disable_ipv6 = 1
To summarize, the /etc/sysctl.conf file must have the following changes:
vm.max_map_count=262144net.ipv6.conf.all.disable_ipv6=1net.ipv6.conf.default.disable_ipv6=1
Save the above changes and then run sudo sysctl -p to apply these settings without restarting the system.
Install the Docker engine
Docker Engine is a containerization technology for building and containerizing applications. Docker Engine acts as a client-server application with:
- A server with a long-running daemon process
dockerd. - APIs which specify interfaces that programs can use to talk to and instruct the Docker daemon.
- A command line interface (CLI) client
docker
To install the docker engine, follow the OS specific steps below. For, additional information related to the installation of the docker engine can be found at:
Ubuntu
Setup the repository
Update the apt package index and install packages to allow apt to use a repository over HTTPS
sudo apt-get install \ca-certificates \curl \gnupg \lsb-release
Add Docker's official GPG Key
sudo mkdir -p /etc/apt/keyringscurl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg
Use the following command to setup the repository
echo \"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/ubuntu \$(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
Install the docker engine
- Update the apt package index
sudo apt-get update
Note: If you receive a GPG error when running apt-get update, then follow the steps below. Your default umask may be incorrectly configured, preventing detection of the repository public key file.
sudo chmod a+r /etc/apt/keyrings/docker.gpgsudo apt-get update
- Install the Docker engine,
containerd, and Docker compose plugin
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-compose-plugin
CentOS 8 Stream / RHEL 8.7+
Setup the repository
Install the yum-utils package (which provides the yum-config-manager utility) and set up the stable repository
yum install -y yum-utilsyum-config-manager \--add-repo \https://download.docker.com/linux/centos/docker-ce.repo
Install the Docker engine
Install the latest version of Docker Engine and containerd. The next step is to start the engine.
yum install docker-ce docker-ce-cli containerd.iosystemctl start dockersystemctl enable docker.servicesystemctl enable containerd.service
Install Docker compose
Compose is a tool for defining and running multi-container Docker applications such as OpenIAM. With Compose, you use a YAML file to configure your application’s services. Then, with a single command, you create and start all the services from your configuration. The procedure described below installs version 1.28.2 of Docker Compose on your system
- Run the command below to download the current stable release of Docker Compose
curl -L "https://github.com/docker/compose/releases/download/1.28.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
- Apply executable permissions to the binary
chmod +x /usr/local/bin/docker-compose
- To check the version of docker compose, run the command below
docker-compose --version
Verify that Docker engine is installed correctly
Run the hello-world image.
docker run hello-world
Note: If you get the following response when running docker run hello-world, then use the work-around below:
Status: Downloaded newer image for hello-world:latest docker: Error response from daemon: cgroups: cgroup mountpoint does not exist: unknown. ERRO[0001] error waiting for container: context canceled
Solution:
mkdir /sys/fs/cgroup/systemdmount -t cgroup -o none,name=systemd cgroup /sys/fs/cgroup/systemddocker run hello-world
After successfully running the hello-world test, we can proceed to installing the application.
log in to Docker hub using the command shown below. Use our hub.docker.com credentials.
Installing the OpenIAM Application
The installation process allows for a significant amount of flexibility. The steps below describe the minimum number of parameters which need to be configured to install on a single VM. Additional details in the sections referenced by the table below. If you are new to OpenIAM, we recommend starting with the simpler path with a more limited set of options.
Clone the OpenIAM Docker repository
Next, we need to clone the "OpenIAM docker compose" repository from OpenIAM's Git Repository. This project contains scripts that set environment variables, start and stop the container services. To clone the repository, follow the steps below.
They should be performed in a Linux terminal window.
mkdir -p /usr/local/openiamcd /usr/local/openiamgit clone https://bitbucket.org/openiam/openiam-docker-compose.gitcd openiam-docker-compose/git checkout RELEASE-4.2.1.7
The cloned repository will contain the following scripts.
| Script | Description |
|---|---|
| env.sh | File containing environment variables. The required environment variables can be updated and added in this file. The env.sh file is sourced during the installation process and the export statements in this file are executed. |
| setup.sh | Script for setting up and updating the OpenIAM configuration. During the initial OpenIAM deployment, this script initializes the network and pulls the latest images from the OpenIAM repository (openiamdocker) on Docker Hub. When updating the OpenIAM deployment, running this script pulls newer images from the OpenIAM repository on Docker Hub |
| startup.sh | Script for starting up the OpenIAM instance.When updating the OpenIAM deployment, running this script updates the configuration on your system with the latest release updates. |
| Warning: Please do not modify this script in any way. | |
| shutdown.sh | Script for shutting down all OpenIAM stacks, except volumes. |
| teardown.sh | Script for tearing down all OpenIAM stacks, volumes, and networks. |
| generate.cert.sh | Script to generate certificates or Vault authentication. |
Additional configuration options
| Section | Description |
|---|---|
| Yaml Files | YAML configuration files are provided for the services and infrastructure components used within OpenIAM. These files provide configuration information for the containers. |
| Configuration options | Configuration options which will be used during installation. |
Set the community edition flag
To ensure that the following steps pull the correct container images, update the /usr/local/openiam/openiam-docker-compose/env.sh file so the
- Production tag is referenced by setting the
BUILD_ENVIRONMENT="dev"to BUILD_ENVIRONMENT="prod" IMAGE_SUFFIXis uncommented
The end result should look like the example below.
...export BUILD_ENVIRONMENT="prod"export IMAGE_SUFFIX="-ce"...
Initialize Vault
OpenIAM uses a Vault in order to store secrets, such as database passwords, redis passwords, etc. Communication with the Vault occurs via a certificate. Follow the steps below to generate the certificate.
- Edit the
/usr/local/openiam/openiam-docker-compose/env.shfile which was downloaded from the openiam-docker-compose project above. - Set the
VAULT_JKS_PASSWORDin the env.sh file. This password can be anything that you want. - Run the command, shown below, to generate a CA Certificate.
- In the Enterprise version, you have the option to use an existing CA Certificate from a trusted CA.
cd /usr/local/openiam/openiam-docker-composesudo ./generate.cert.sh
You should see output similar to the example shown below:
SQL Files existThis script will generate a keypair that vault will use. Make sure to first set VAULT_JKS_PASSWORD in env.shPress enter to continueCertificate request self-signature oksubject=C = CZ, ST = Test, L = Test, O = Test, OU = Test, CN = vaultWarning: -clcerts option ignored with -exportwriting RSA key
Upon successful completion of the above operation, you should also see several certificates related files as shown in the image below.
-rw-r--r-- 1 root root 1302 Jan 29 03:09 vault.ca.crt-rw------- 1 root root 1704 Jan 29 03:09 vault.ca.key-rw-r--r-- 1 root root 1180 Jan 29 03:09 vault.crt-rw-r--r-- 1 root root 985 Jan 29 03:09 vault.csr-rw-r--r-- 1 root root 2 Jan 29 03:09 vault.file.srl-rw------- 1 root root 2579 Jan 29 03:09 vault.jks-rw------- 1 root root 1704 Jan 29 03:09 vault.key-rw------- 1 root root 1704 Jan 29 03:09 vault.no_pem.key-rw------- 1 root root 2579 Jan 29 03:09 vault.p12
Define database ports
Starting with V4.2.0, OpenIAM uses Flyway to manage database schema generation and migrations from one version to the next. This ensures that your database is properly versioned and up-to-date. OpenIAM supports Flyway versioning for MariaDB, PostgreSQL, and MSSQL, and Oracle 12.2+
The env.sh file defines properties which will be used by Flyway.
At a minimum, you will need to define to set the following parameters: To enable Flyway, set the following properties in env.sh
- DB_TYPE - This parameter define the type of database that you will be using as the OpenIAM product repository. My default this value is set to "MariaDB" which is installed by default .
- FLYWAY_OPENIAM_HOST - Host where the OpenIAM database will be residing. This is the primary product schema. If you are using MariaDB or [[PostgreSQL in a docker container, set it to
database - FLYWAY_OPENIAM_PORT - Port where the OpenIAM database will be running. Default ports for the supported databases include:
- MariaDB=3306
- Postgres=5432
- Oracle=1521
- Microsoft SQL Server=1433
- FLYWAY_ACTIVITI_HOST - Host where the Activti database will be residing. Activiti, is the database used by the workflow engine. If you are using MariaDB or PostgreSQL in a docker container, set it to
database - FLYWAY_ACTIVITI_PORT - Port where Activiti database, which is used by the workflow engine, will be running.
Example below shows the settings for MariaDB
export DB_TYPE="MariaDB"...# port of the activiti database. If using mariadb, this is likely '3306'. If using postgres, this is likely '5432'export FLYWAY_ACTIVITI_PORT=3306# host of the activiti database. If using mariadb or postgres in docker, this is likely 'database'export FLYWAY_ACTIVITI_HOST=database# port of the openiam database. If using mariadb, this is likely '3306'. If using mariadb, this is likely '3306'. If using postgres, this is likely '5432'export FLYWAY_OPENIAM_PORT=3306# host of the openiam database. If using mariadb or postgres in docker, this is likely 'database'export FLYWAY_OPENIAM_HOST=database
Initialize Docker Swarm
Docker uses swarms for cluster management and orchestration features of Docker Engine, the technology for containerizing applications. Docker engines participating in a cluster run in the swarm mode. The swarm mode is enabled by either initializing a swarm, as in the command above, or by joining an existing swarm. For more information, see docker swarm and Swarm mode key concepts documentation.
Make sure that you initialize the Docker swarm. Log into Docker and initialize the swarm by entering the following command in a terminal:
sudo docker swarm init
You will see output similar to this:
Swarm initialized: current node (7risfc2161nwzir4a65po3lro) is now a manager.To add a worker to this swarm, run the following command:docker swarm join --token SWMTKN-1-15mdug8xi71uap0dgaayqi2ohhl8qxaaeg7m8k6q015yiuqt0j-6ip90bh1rm2td8y9baoya4qlx 173.231.56.82:2377To add a manager to this swarm, run 'docker swarm join-token manager' and follow the instructions.
Open ports for Docker Swarm
By default, the shell scripts provided by OpenIAM deploy to the docker swarm. You must ensure that the necessary ports are opened otherwise the manager and worker node(s) will not be able to communicate with each other.
Important: Please see this information about ports above 30000 used by the swarm from the load balancing section of Docker documentation: The swarm manager uses ingress load balancing to expose the services you want to make available externally to the swarm. The swarm manager can automatically assign the service a PublishedPort or you can configure a PublishedPort for the service. You can specify any unused port. If you do not specify a port, the swarm manager assigns the service a port in the 30000-32767 range.
Pull the docker images
To setup (and/or update) your configuration, you can run the setup.sh script. This will initialize the network, and pull the latest images from Docker Hub.
For users, familiar with OpenIAM, you can modify the script as required by your internal needs.
- Run the setup.sh script as shown below to pull the docker images form Docker Hub.
sudo ./setup.sh
This process will take several minutes. Upon successful completion, you will see the following lines at the end.
...Digest: sha256:0bb33339f0c06d781eaffb3e78e296f4ad8d1474915e7872e5a9094a8da9ee76Status: Downloaded newer image for openiamdocker/vault-ce:alpine-4.2.1.7-proddocker.io/openiamdocker/vault-ce:alpine-4.2.1.7-prod+ docker pull openiamdocker/vault-bootstrap-ce:alpine-4.2.1.7-prodalpine-4.2.1.7-prod: Pulling from openiamdocker/vault-bootstrap-ce2408cc74d12b: Pull completee23a669031d3: Pull complete58d03b857787: Pull complete57690cd8fe01: Pull completed7ddacc22990: Pull complete601a9aa2e412: Pull complete7286a0f9c14c: Pull complete064aa39d2270: Pull complete9ac4bee4a2c2: Pull complete6f8406638991: Pull complete1a60362ddd04: Pull completeaf7fa38835b7: Pull complete45dc28dcb82d: Pull completeDigest: sha256:ef2fadb1bdeded40372a7caf5346e10f9a75b79f4a63db21596ede03c2000ca8Status: Downloaded newer image for openiamdocker/vault-bootstrap-ce:alpine-4.2.1.7-proddocker.io/openiamdocker/vault-bootstrap-ce:alpine-4.2.1.7-prod+ docker pull openiamdocker/ui-ce:debian-4.2.1.7-proddebian-4.2.1.7-prod: Pulling from openiamdocker/ui-ce9621f1afde84: Already exists646a8f97c6a8: Already exists111ef215ea01: Pulling fs layerfb4ccfb62028: Pulling fs layer5780a89424ca: Pulling fs layerac405e1bcaf1: Pulling fs layerc8599e3b267a: Pulling fs layer45c751205584: Pulling fs layerd073c823bebc: Pulling fs layer5cc21ea2eea5: Pull completeba7abde15e29: Pull completec984fa56e5a0: Pull completec384c82e524c: Pull complete2f54ac6cc048: Pull completee571d9818056: Pull complete0a0cdfc4b537: Pull completec738260940dc: Pull complete9daad2955b32: Pull complete6221693a634b: Pull complete7dbe84e43ad2: Pull complete97e706f13a86: Pull complete4cae4fc929c4: Pull complete43828485f417: Pull complete56bc0ddee1a0: Pull complete3611f7603357: Pull complete2b9b44628925: Pull complete8ac3b6158823: Pull complete9a5c45fad651: Pull completea2e069d4323a: Pull completec15344a40a9b: Pull complete8b829f3b502c: Pull completed0c9bb174905: Pull completeDigest: sha256:91626efa38c2580452f4c7f55732ff4c3038c0bdd1f143012ae209c7611dbcf5Status: Downloaded newer image for openiamdocker/ui-ce:debian-4.2.1.7-proddocker.io/openiamdocker/ui-ce:debian-4.2.1.7-prod
Start the OpenIAM Application
Now you are ready to start the OpenIAM containers. Run the startup.sh script to initiate the startup process
sudo ./startup.sh
You should see output similar to the example below
root@localhost:/usr/local/openiam/openiam-docker-compose# ./startup.shSQL Files existUsing MariaDB as the database type...Nothing found in stack: flywayetcd_storagevault_server_storagevault_client_storageconnector_data_storagefilebeat-storageopeniam-janusgraph-storageupload_storageUnable to find image 'busybox:latest' locallylatest: Pulling from library/busybox9ad63333ebc9: Pull completeDigest: sha256:6d9ac9237a84afe1516540f40a0fafdc86859b2141954b4d643af7066d598b74Status: Downloaded newer image for busybox:latestCreating service etcd_etcdCreating service vault_vaultCreating service vault-bootstrap_vault_bootstrapCreating service curator_curatorCreating service openiam-elasticsearch-storage_serviceCreating service openiam-jks-storage_serviceCreating service openiam-activiti-storage_serviceCreating service openiam-rabbitmq-storage_serviceCreating service openiam-iamscripts-storage_serviceCreating service redis_serviceCreating service elasticsearch_serviceCreating service cassandra_cassandraWaiting for cassandra to become running, so that we can bring up janusgraphCreating service janusgraph_serviceCreating service rabbitmq_serviceopeniam-mysql-storage_storageCreating service database_databaseCreating service flyway_flywayCreating service openiam_device-managerCreating service openiam_auth-managerCreating service openiam_groovy_managerCreating service openiam_reconciliationCreating service openiam_email-managerCreating service openiam_synchronizationCreating service openiam_business-rules-managerCreating service openiam_idmCreating service openiam_esbCreating service openiam_workflowCreating service ui_uiCreating service ldap-connector_serviceCreating service rproxy_rproxy
Watch the container startup process
The containers may take 8 to 15 minutes (depending your environment) to startup completely. You can watch the start up process using the command below. Note, that the UI container will take sometime and be among the last to start up as it has dependencies on other components being up first.
watch -n 5 'docker ps'
You should see output similar to the example below when all containers have started successfully
Every 5.0s: docker ps localhost: Tue Jan 30 02:46:06 2024CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMESd77654ad06bb openiamdocker/synchronization-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_synchronization.uxe0l47z26ubeags0f6i2h9yt.x9tb0r4zv5ngp7ezpwxd2gkhw4ebcb5b5ccb5 openiamdocker/redis-ce:debian-4.2.1.7-prod "redis.sh /run.sh" 3 hours ago Up 3 hours (healthy) 6379/tcp redis_service.1.uyc7pw0n0cqlcxta2svqud46c417519dd58bd openiamdocker/groovy-manager-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_groovy_manager.uxe0l47z26ubeags0f6i2h9yt.ugf9okpghfwrsbkbeayr2151u571bbb9cf8b7 openiamdocker/auth-manager-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_auth-manager.uxe0l47z26ubeags0f6i2h9yt.sxgdv885fhs8kdhe42ujz9fns90d6b5611335 openiamdocker/mariadb-ce:debian-4.2.1.7-prod "init.sh /opt/bitnam…" 3 hours ago Up 3 hours (healthy) 3306/tcp database_database.1.36foh88mgh2isusgypvq4mds719b6100351f3 openiamdocker/workflow-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_workflow.uxe0l47z26ubeags0f6i2h9yt.ja1w84wftb6nej2vlef2lkq6y93ab34fe4c91 openiamdocker/device-manager-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_device-manager.uxe0l47z26ubeags0f6i2h9yt.mefg80i4hsn7dx8hlb99s9yb8d6efe734a8c4 openiamdocker/rabbitmq-ce:alpine-4.2.1.7-prod "docker-entrypoint.s…" 3 hours ago Up 3 hours (healthy) 4369/tcp, 5671-5672/tcp, 15691-15692/tcp, 25672/tcp rabbitmq_service.1.doci1z5ypha5uahoj11zvn5s1e2395b97271a openiamdocker/reconciliation-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_reconciliation.uxe0l47z26ubeags0f6i2h9yt.3jm01yf0sxmasjyhxlot909hcd1c4abdf8eca openiamdocker/idm-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_idm.uxe0l47z26ubeags0f6i2h9yt.1r90ew19ev48ra96pqz3ufe9w9cf6779c52a8 openiamdocker/ldap-connector-rabbitmq-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) ldap-connector_service.uxe0l47z26ubeags0f6i2h9yt.m0muld83kpqgrd7leklb44lz0903d5a9ae775 openiamdocker/email-manager-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) openiam_email-manager.uxe0l47z26ubeags0f6i2h9yt.626qka38iht4ggcb917iw3wkodf03660737a4 openiamdocker/rproxy-ce:debian-4.2.1.7-prod "httpd-foreground" 3 hours ago Up 3 hours (healthy) 0.0.0.0:80->80/tcp, 443/tcp rproxy_rproxy.uxe0l47z26ubeags0f6i2h9yt.4m6f8h5sv1khf0v8ncga356ki4cceeb5c242e openiamdocker/janusgraph-ce:debian-4.2.1.7-prod "init.sh janusgraph" 3 hours ago Up 3 hours (healthy) 8182/tcp janusgraph_service.1.8czw1aew0vr95cfru5ms9wumhdc489e4bcf07 bitnami/cassandra:3.11.10 "/opt/bitnami/script…" 3 hours ago Up 3 hours (healthy) 7000/tcp, 9042/tcp cassandra_cassandra.1.n80icn1rvgxo30787pqporibac23454f6c49d openiamdocker/vault-ce:alpine-4.2.1.7-prod "docker-entrypoint.s…" 3 hours ago Up 3 hours (healthy) 8200/tcp vault_vault.1.it6b7du4vp2j9j9nj00d4vemk07fda75ba205 openiamdocker/elasticsearch-ce:debian-4.2.1.7-prod "init.sh" 3 hours ago Up 3 hours (healthy) 9200/tcp, 9300/tcp elasticsearch_service.uxe0l47z26ubeags0f6i2h9yt.jg4j5rb0hb0cvpdcbu98019ap443ffe2aaddd openiamdocker/ui-ce:debian-4.2.1.7-prod "docker-entrypoint.s…" 3 hours ago Up 3 hours (healthy) 8080/tcp ui_ui.uxe0l47z26ubeags0f6i2h9yt.g4fh9r8g1sxabeq5c04zcjhw75cbfadbc86ac openiamdocker/esb-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) 9080/tcp openiam_esb.uxe0l47z26ubeags0f6i2h9yt.ct9wt15av67ub9k486kirjjck690529bf3076 openiamdocker/business-rule-manager-ce:debian-4.2.1.7-prod "docker-entrypoint.sh" 3 hours ago Up 3 hours (healthy) 9080/tcp openiam_business-rules-manager.uxe0l47z26ubeags0f6i2h9yt.2pkewzi8f32gvwl352ugi7odj70c3c5a7ff51 bitnami/etcd:3.3.13 "/entrypoint.sh etcd" 3 hours ago Up 3 hours 2379-2380/tcp etcd_etcd.1.xkby0e1syswnk1kcjama6pear
Validate the startup
curl -k -I -L http://127.0.0.1/idp/login
You should see output similar to the example below
HTTP/1.1 200Date: Tue, 30 Jan 2024 02:46:46 GMTServer: ApacheReport-To: { "group": "csp-endpoint", "max_age": 10886400, "endpoints": [ { "url": "http://127.0.0.1/selfservice/csp/report" } ] }Content-Security-Policy: default-src 'self' blob: data: 'unsafe-inline' 'unsafe-eval'; script-src 'self' 'unsafe-inline' 'unsafe-eval' apis.google.com; style-src 'self' 'unsafe-inline' 'unsafe-eval' *; form-action 'self' 'unsafe-inline' 'unsafe-eval' *; img-src 'self' data:; font-src 'self' *; report-uri /selfservice/csp/report; report-to csp-endpointReferrer-Policy: strict-originAccess-Control-Allow-Origin: *X-Frame-Options: sameoriginX-Content-Type-Options: nosniffX-XSS-Protection: 1; mode=blockCache-Control: no-cachePragma: no-cacheExpires: Wed, 31 Dec 1969 23:59:59 GMTX-UA-Compatible: IE=EmulateIE10x-openiam-force-auth: falsex-openiam-login-uri: /idp/loginContent-Type: text/html;charset=UTF-8Content-Language: en-USContent-Length: 4666Set-Cookie: SESSION=N2EyYTQ0MjMtZmNlMC00OTlmLTg1NjItNDNmMjBmMjI1MmMy; Path=/; HttpOnly; SameSite=LaxVary: Accept-Encoding
The application is now operational and you can login.
First time login
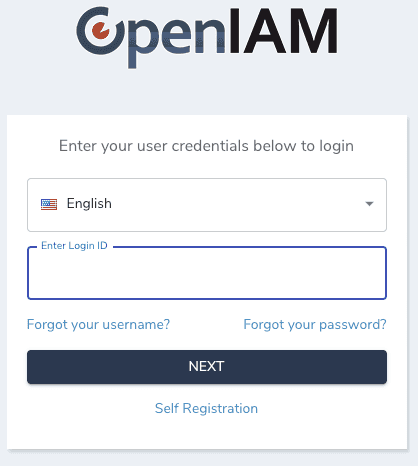
The final validation of our deployment is to be able to login to the OpenIAM web applications. To do this, must first find the IP address of our VM.
Next open your browser (preferably Chrome or Firefox), and hit:
http://[ip address of your installation ]/webconsole
Use the following credentials for the first-time login:
Username: sysadminPassword: passwd00
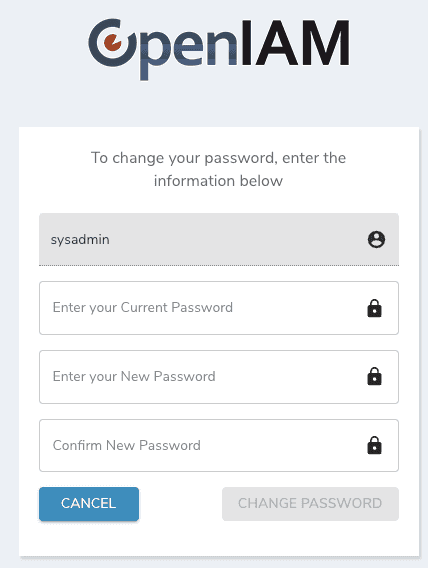
The next screen will ask you to change the default password. As you enter your new password, you will see the password policy on the side. You password must align with this policy. You will be able to change both the password and the policy later
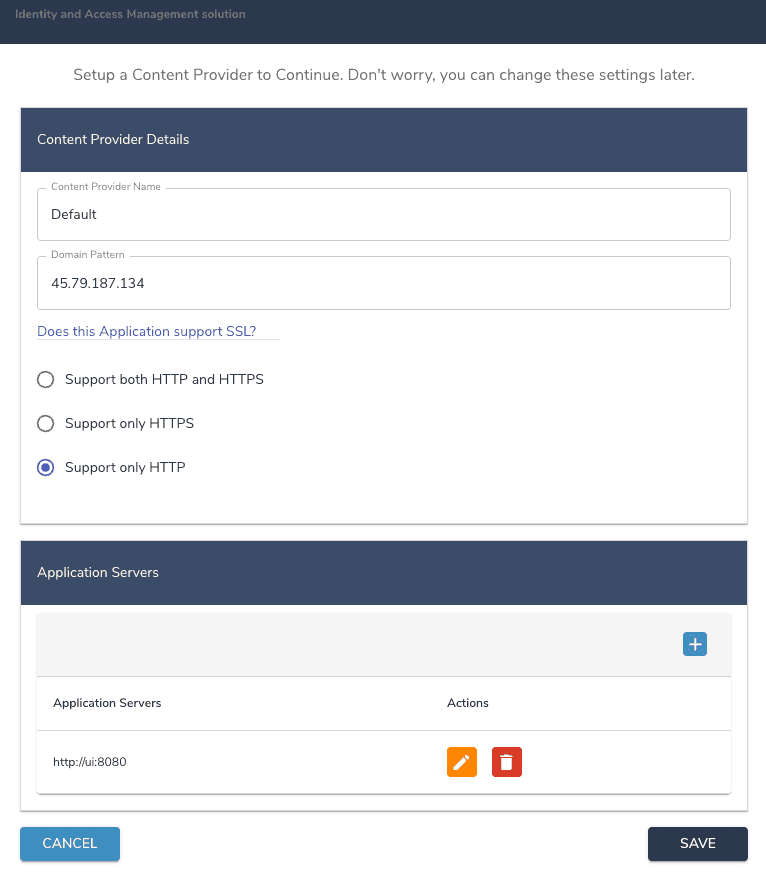
The next step is to define a content provider using the screen shown below. A Content provider is an alias that represents a domain. Associated with the content provider can be UI themes, authentication policies, etc. The table below describes the fields on this screen.
| Name | Description |
|---|---|
| Content Provider Name | You can think of a content provider an “alias” which represents a domain. This is described in more detail in the OpenIAM documentation. For this setup, please enter a value such as : Default CP |
| Domain Pattern | This value is defaulted in. It should be the IP address or host DNS name of the instance where OpenIAM has been installed |
| Application supports SSL? | This configuration determines if the OpenIAM application will be accessed over HTTP or HTTPS. Unless, you have already configured the certificate, select Support on HTTP. You will be able to update this configuration later. |
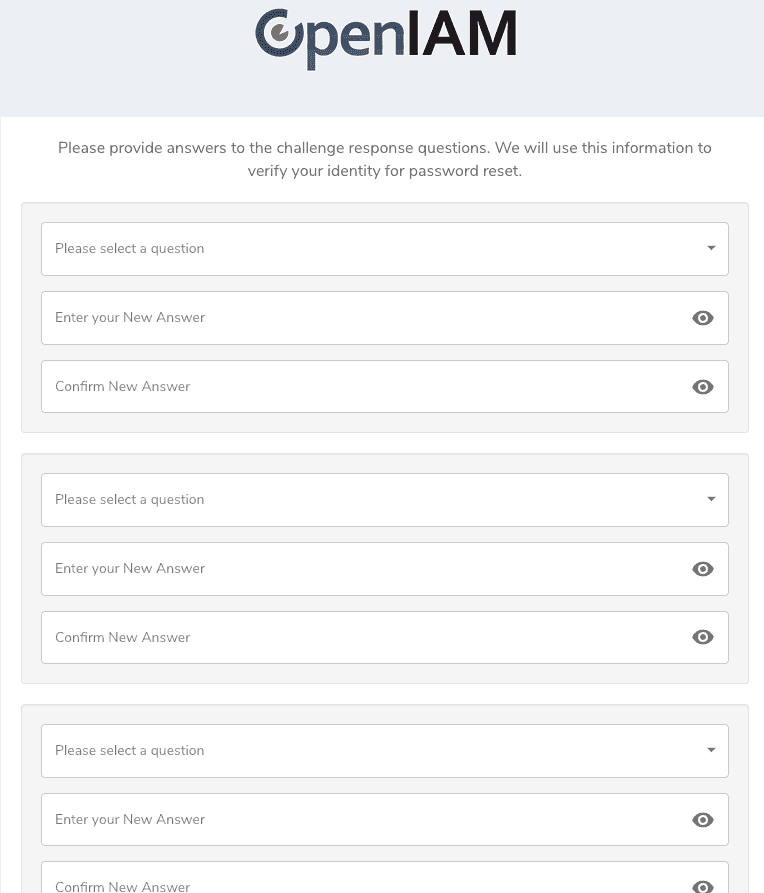
After setting the content provider, you will be taken to the challenge questions page. These questions will be used to reset your admin account if you lock yourself out. Make a note of your answers.
After completing the above steps, you will be taken the admin console landing page shown below. Allow the system about 5 min to refresh in the internal cache and then you can proceed to configure your solution.
Frequently used commands with Docker
The following commands are frequently used with Docker.
| Command | Description |
|---|---|
| ./startup.sh | Starts the OpenIAM Docker containers |
| ./shutdown.sh | Stops the OpenIAM Docker containers |
| Ensure that all containers have stopped before restarting. You can validate that the containers have stopped using the docker ps command | |
| docker ps | Shows all the containers which are running |
| watch -n 5 'docker ps' | Allows you to observe the docker containers. The view is refreshed every -n seconds. |
| docker logs [container id] | Shows the logs related to the Container ID. You can get the Container ID from the docker ps command. |
| docker exec -it [container id] bash | Allows you to connect to the container |
| docker restart -t [time][container id] | Allows you to restart a container. Time is the number seconds to wait after stopping a container, but its started again. |